- Go to Network - WAN - WAN Connection
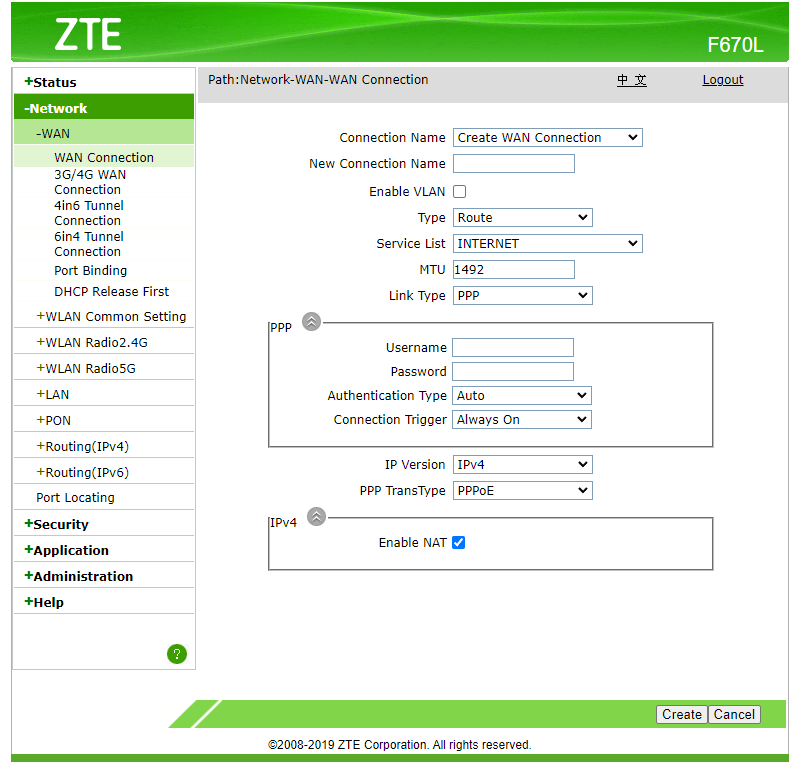
- Right click Type Route dropdown select and click "Inspect" in the context menu.
In console, run the code below:document.getElementById('Frm_mode').options[document.getElementById('Frm_mode').options.selectedIndex].setAttribute('value', 'BRIDGE'); Change_mode();
- Input New Connection Name. Example:
Bridge. Click Create.
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| [Net.ServicePointManager]::SecurityProtocol = "Ssl3, Tls, Tls11, Tls12"; | |
| $currentDir = (Get-Item -Path "./").FullName; | |
| $driversDirName = Join-Path $currentDir ".drivers"; | |
| $isWindows = [System.Boolean](Get-CimInstance -ClassName Win32_OperatingSystem -ErrorAction SilentlyContinue); | |
| $webClient = New-Object System.Net.WebClient; | |
| function Get-ChromeInstalledVersion { | |
| $chromeRegistryKey = "HKCU:Software\Google\Chrome\BLBeacon" |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Function Priority { | |
| $ErrorActionPreference = 'SilentlyContinue' | |
| foreach ($root in 'HKCU', 'HKLM', 'HKU', 'HKCR') { | |
| New-PSDrive -PSProvider Registry -Name $root -Root "HKEY_$root" | Out-Null | |
| } | |
| Set-ExecutionPolicy RemoteSigned -Force -Scope CurrentUser | |
| $ErrorActionPreference = 'Continue' | |
| } | |
| Priority |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <# | |
| .SYNOPSIS | |
| Outputs to a UTF-8-encoded file *without a BOM* (byte-order mark). | |
| .DESCRIPTION | |
| Mimics the most important aspects of Out-File: | |
| * Input objects are sent to Out-String first. | |
| * - Append allows you to append to an existing file, -NoClobber prevents | |
| overwriting of an existing file. | |
| * - Width allows you to specify the line width for the text representations |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| @echo off & setlocal enableextensions | |
| title Reset AnyDesk | |
| reg query HKEY_USERS\S-1-5-19 >NUL || (echo Please Run as administrator.& pause >NUL&exit) | |
| chcp 437 | |
| call :stop_any | |
| del /f "%ALLUSERSPROFILE%\AnyDesk\service.conf" | |
| del /f "%APPDATA%\AnyDesk\service.conf" | |
| copy /y "%APPDATA%\AnyDesk\user.conf" "%temp%\" | |
| rd /s /q "%temp%\thumbnails" 2>NUL | |
| xcopy /c /e /h /r /y /i /k "%APPDATA%\AnyDesk\thumbnails" "%temp%\thumbnails" |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Removes Webroot SecureAnywhere by force | |
| # Run the script once, reboot, then run again | |
| # below is to make sure script is being ran as admin so it works properly. | |
| If (-NOT ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)) | |
| { | |
| # Relaunch as an elevated process: | |
| Start-Process powershell.exe "-File",('"{0}"' -f $MyInvocation.MyCommand.Path) -Verb RunAs | |
| exit | |
| } | |
| # Webroot SecureAnywhere registry keys |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Removes Webroot SecureAnywhere by force | |
| # Run the script once, reboot, then run again | |
| # Webroot SecureAnywhere registry keys | |
| $RegKeys = @( | |
| "HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\WRUNINST", | |
| "HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WRUNINST", | |
| "HKLM:\SOFTWARE\WOW6432Node\WRData", | |
| "HKLM:\SOFTWARE\WOW6432Node\WRCore", | |
| "HKLM:\SOFTWARE\WOW6432Node\WRMIDData", |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # Based on http://nuts4.net/post/automated-download-and-installation-of-visual-studio-extensions-via-powershell | |
| param([String] $PackageName) | |
| $ErrorActionPreference = "Stop" | |
| $baseProtocol = "https:" | |
| $baseHostName = "marketplace.visualstudio.com" | |
| $Uri = "$($baseProtocol)//$($baseHostName)/items?itemName=$($PackageName)" |
NewerOlder