I hereby claim:
- I am c633 on github.
- I am pqcrypt (https://keybase.io/pqcrypt) on keybase.
- I have a public key whose fingerprint is E743 F730 678B B0C7 6777 72FE 049A D8DF E5EA 1AFC
To claim this, I am signing this object:
I hereby claim:
To claim this, I am signing this object:
Once in a while, you may need to cleanup resources (containers, volumes, images, networks) ...
// see: https://github.com/chadoe/docker-cleanup-volumes
$ docker volume rm $(docker volume ls -qf dangling=true)
$ docker volume ls -qf dangling=true | xargs -r docker volume rm
scrapped from @x0rz,@etlow,@Dinosn,@hackerfantastic,@highmeh,@cyb3rops and others
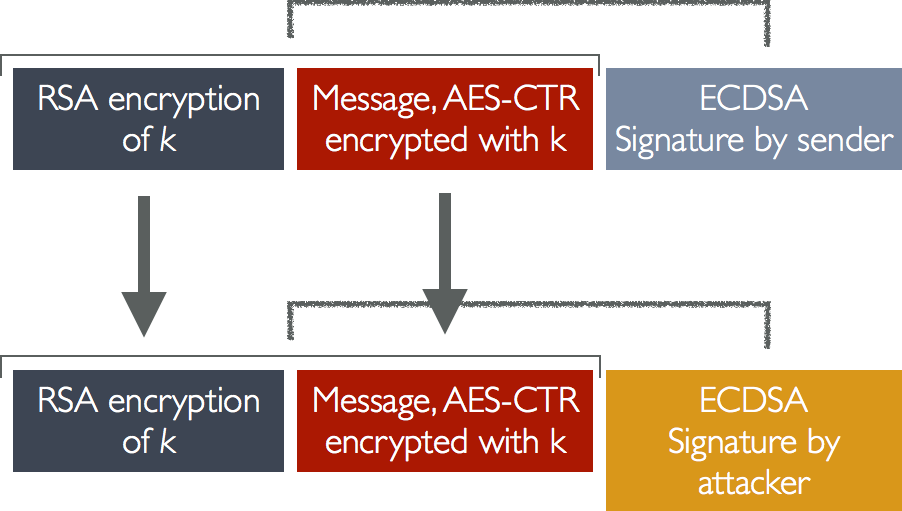
Apple iMessage uses MAC-less encryption with malleable ciphertext. That, however, is not the worst part, and neither are the small 1280-bit RSA keys.
The worst part is that iMessage uses an independent ECDSA signature key, which is not only "independent" due to being a separate/different key from the AES encryption key, but also due to not being involved in the encryption/decryption stage at all!
| #!/usr/bin/env python | |
| from z3 import * | |
| def display_model(m): | |
| block = {} | |
| for x in m: | |
| if 'b' in str(x): | |
| block[ord(str(x)[-1:])] = int(str(m[x])) |
| #!/usr/bin/env sage -python2 | |
| from sage.all import * | |
| e1 = long(599703852157208324988436697659896404638315905290324375700570316485421693) | |
| e2 = long(2021187385200166516022746434619391941987919206967476592818217288363509) | |
| print 'gcd(e1, e2) = ' + str(gcd(e1, e2)) # should be 1 | |
| n = long(108039548283467910018636019706918049787296862983920390620425680109149061265582938100265640505395436176923520902062289606379329490555998996693285930619495040456388113166495283026905991110314710632437395833112529488024010984327573108928719840003018232385552027586272040584786259207191357206321725581066222359269709853312236804681275337051689984480610347322381805920314518020927280061535012383180989715215061621017100281215170089223279840979641688194933238176625422507335413025975742216947757245112001827202742177202602339368271393570814426349) |
| ''' | |
| ./hash_extender --data VVNFUk5BTUU9YWRtaW4AQmlvZ3JhcGh5PWFkbWkAUk9MRT0w --secret 16 --append AFJPTEU9MQ== --signature 89542f421e21de8edfcf39ec0e88b29b --format md5 | |
| Type: md5 | |
| Secret length: 16 | |
| New signature: 8c8a2d7f702abae1fb78766aa8694ebd | |
| New string: 56564e46556b3542545555395957527461573441516d6c765a334a68634768355057466b62576b41556b394d525430778000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000000000041464a50544555394d513d3d | |
| ''' | |
| from pwn import * | |
| s = remote("192.168.1.101", 31330) |
| #include <stdio.h> | |
| #include <stdlib.h> | |
| #include <string.h> | |
| #include <stdint.h> | |
| int dword_804B16C, dword_804B170, dword_804B174, dword_804B178, dword_804B17C, dword_804B180; | |
| int pos = 0; | |
| int v11; | |
| int v12; |
| #include <stdlib.h> | |
| #include <stdio.h> | |
| void main(int argc, char *argv[]) | |
| { | |
| if( argv[1][0] == 'f' ) { | |
| if( argv[1][1] == 'o' ) { | |
| if( argv[1][2] == 'o' ) { | |
| if( argv[1][3] == '\x00' ) { | |
| printf( "good password\n" ); |
| ########################################################################### | |
| # Rotating bits (tested with Python 2.7) | |
| from __future__ import print_function # PEP 3105 | |
| # max bits > 0 == width of the value in bits (e.g., int_16 -> 16) | |
| # Rotate left: 0b1001 --> 0b0011 | |
| rol = lambda val, r_bits, max_bits: \ | |
| (val << r_bits%max_bits) & (2**max_bits-1) | \ |