A simple implementation.
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| import pandas as pd | |
| import matplotlib.pyplot as plt | |
| def draw_candlestick(data, time_axis, window_size, **kwargs) -> plt.Figure: | |
| """ | |
| Draws a candlestick chart. | |
| Parameters: | |
| data (list or np.ndarray): Continuous data points. | |
| time_axis (list or np.ndarray): Corresponding time points (timestamps or discrete steps). |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| from typing import Literal | |
| import pandas as pd | |
| def get_ensembl_mappings( | |
| genes: list[str], | |
| organism: str = "hsa", | |
| server: Literal["www", "eu", "uswest", "asia", "gprofiler"] = "asia", | |
| ) -> pd.DataFrame: |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| def ens2seq(ensembl_id: str) -> str: | |
| """Converts ensembl gene id to protein sequence | |
| @ensembl_id: str, ensembl gene id | |
| """ | |
| uri = f"https://rest.uniprot.org/uniprotkb/stream?" | |
| query = f"({ensembl_id}) AND (reviewed:true)" | |
| params = { | |
| "compressed": "false", |
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
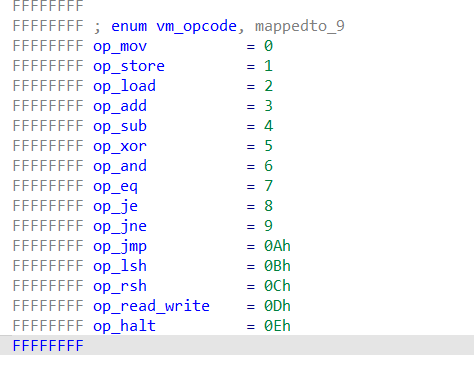
We are given a virtual machine binary called run, and a custom binary for it called VM. It has 16 registers and a flat memory. Below is the opcodes of this VM.
Then, we should disassemble the given program to see what's going on.
disasm.py disassembles the custom binary VM into disassembly.S. Take a look at it.
This is a write-up for task segfault labyrinth in google ctf 2022
The problem is consisted with a single amd64 binary. What it does is simple. It just runs your shellcode with some limitations. For example, there is a seccomp filter which prevents you from getting new file descriptors.
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #ifndef __LIB_COLORS_H | |
| #define __LIB_COLORS_H | |
| #ifndef NO_COLORS | |
| /** | |
| * ANSI Escapes for Normal Colors. | |
| */ | |
| #define BLK(TEXT) "\x1b[30m"TEXT"\x1b[0m" | |
| #define RED(TEXT) "\x1b[31m"TEXT"\x1b[0m" |
NewerOlder