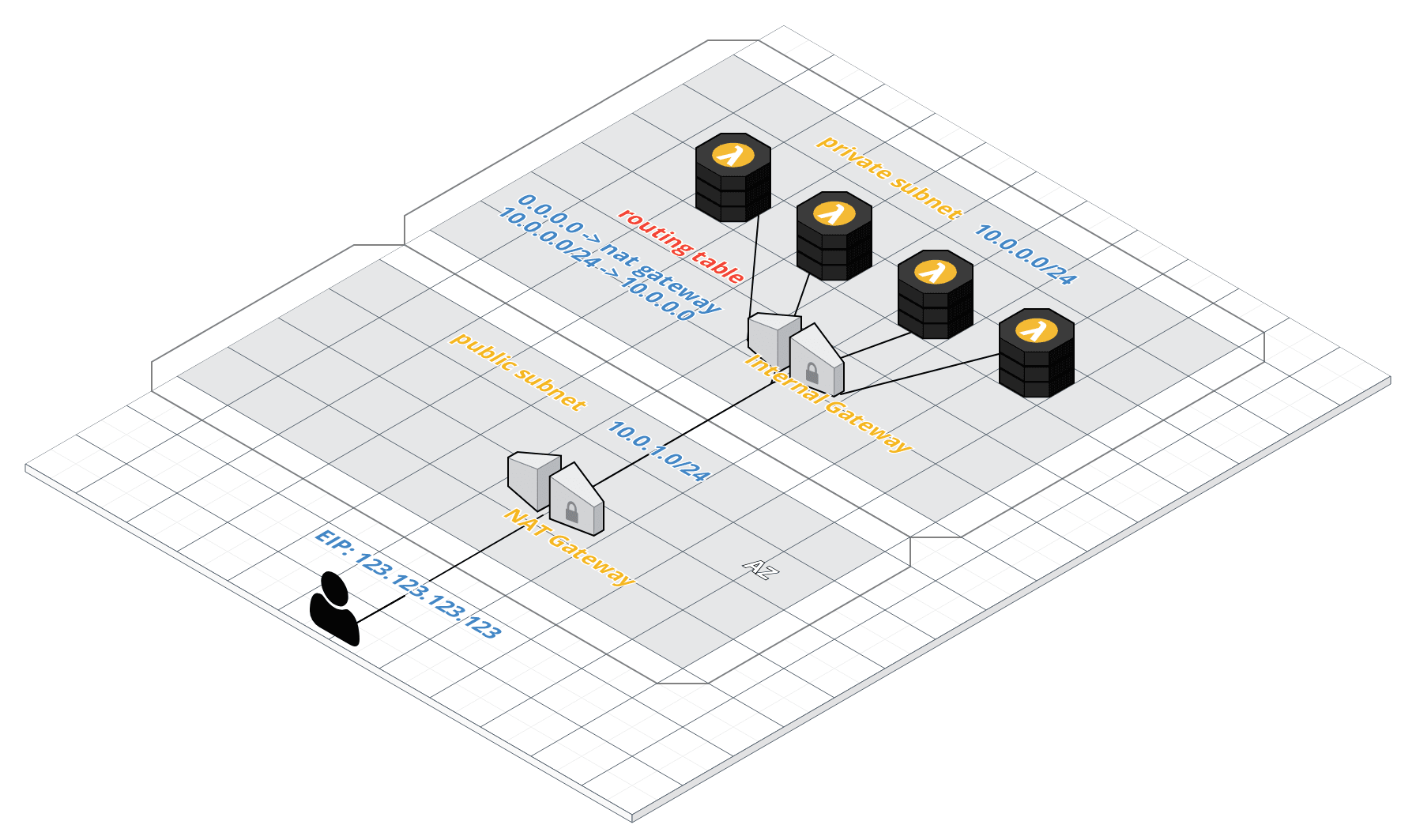
Sometimes, we need a static IP for accessing a private service since it has several firewall rules to avoide malcious attacks. In this case, we can create a NAT gateway on AWS and assign a static IP for this gateway. Therefore, we can use this public IP address to access our private service. This note tries to demonstrate how to create a NAT gateway on AWS VPC.
- one private subnet
- one public subnet
- one internal gateway
- one NAT gateway
- Elastic IP (public static IP)
- 2 routing tables
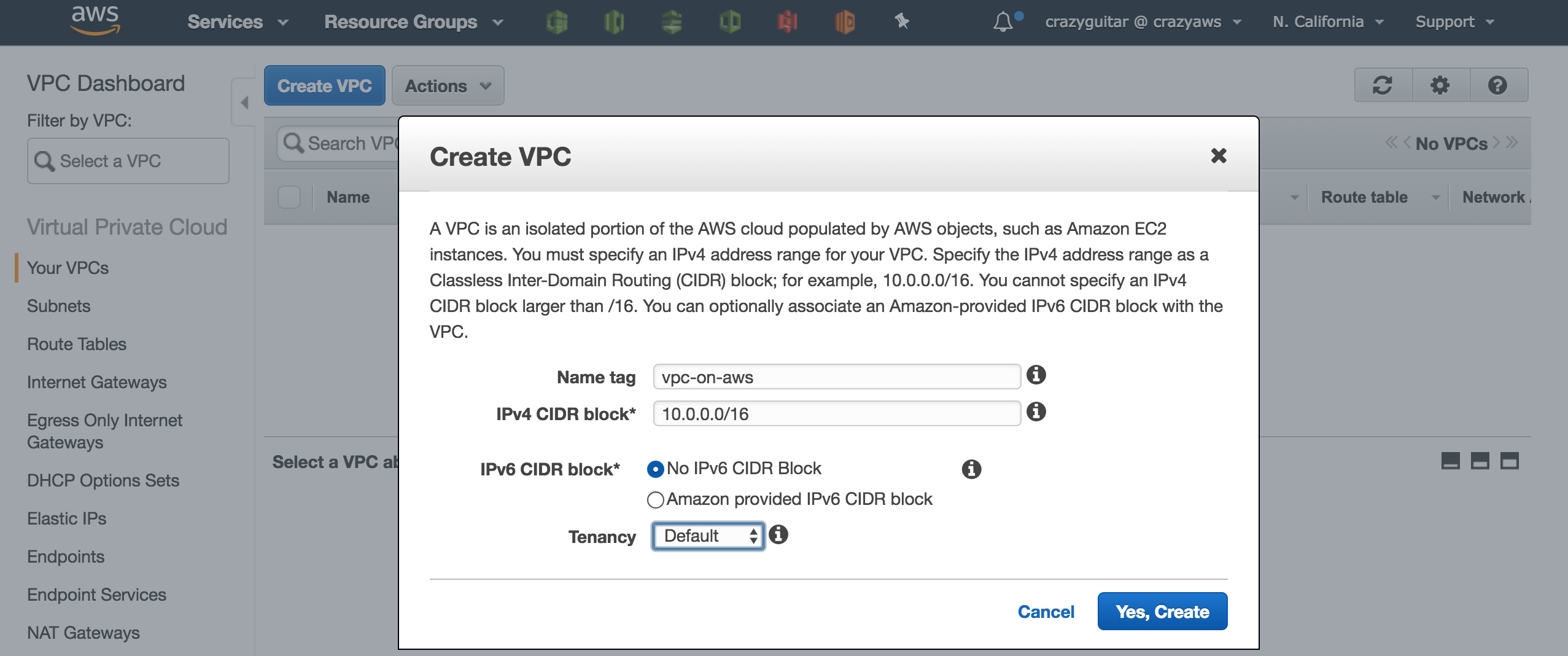
- Go to VPC console and click
Your VPCsfor creating a VPC on AWS - Click
Create VPCand fill the information as following figure.
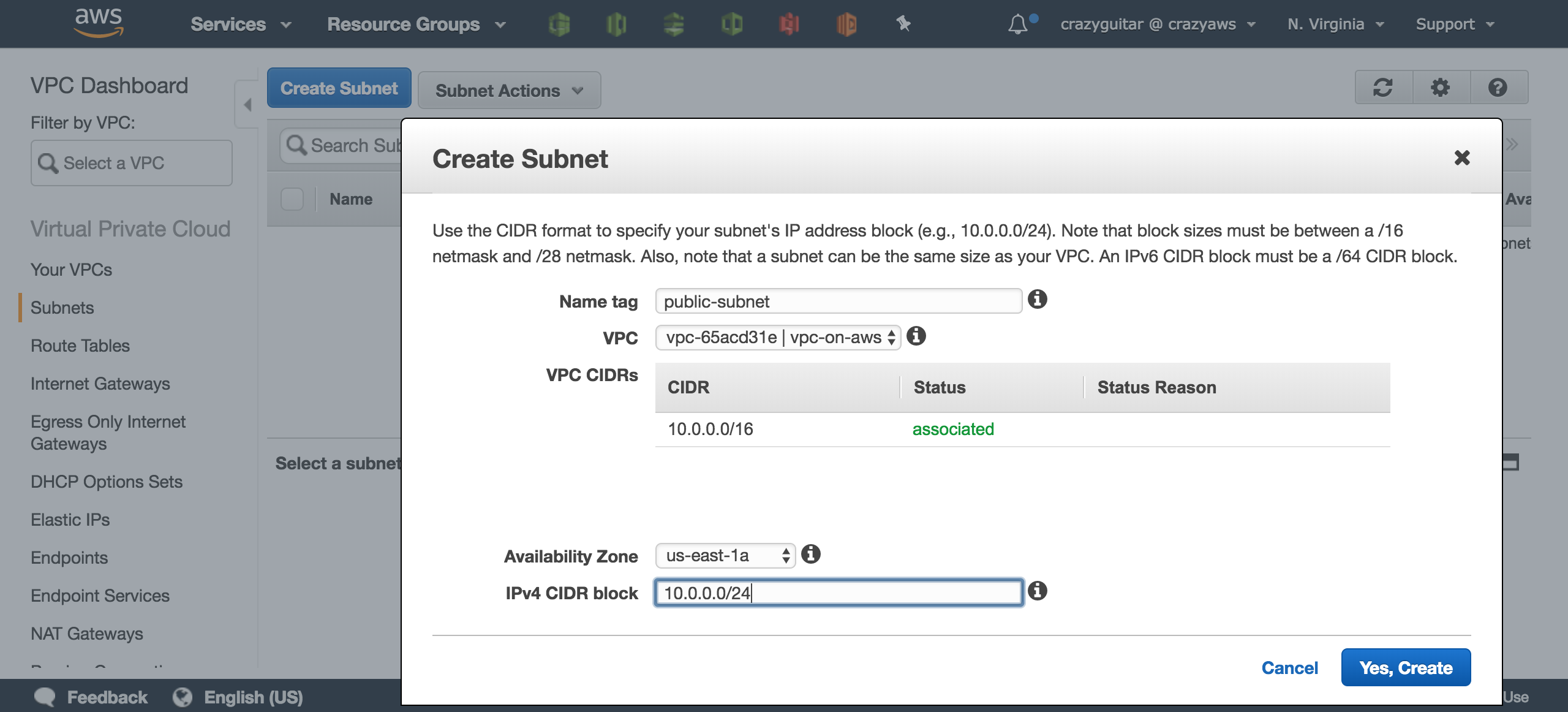
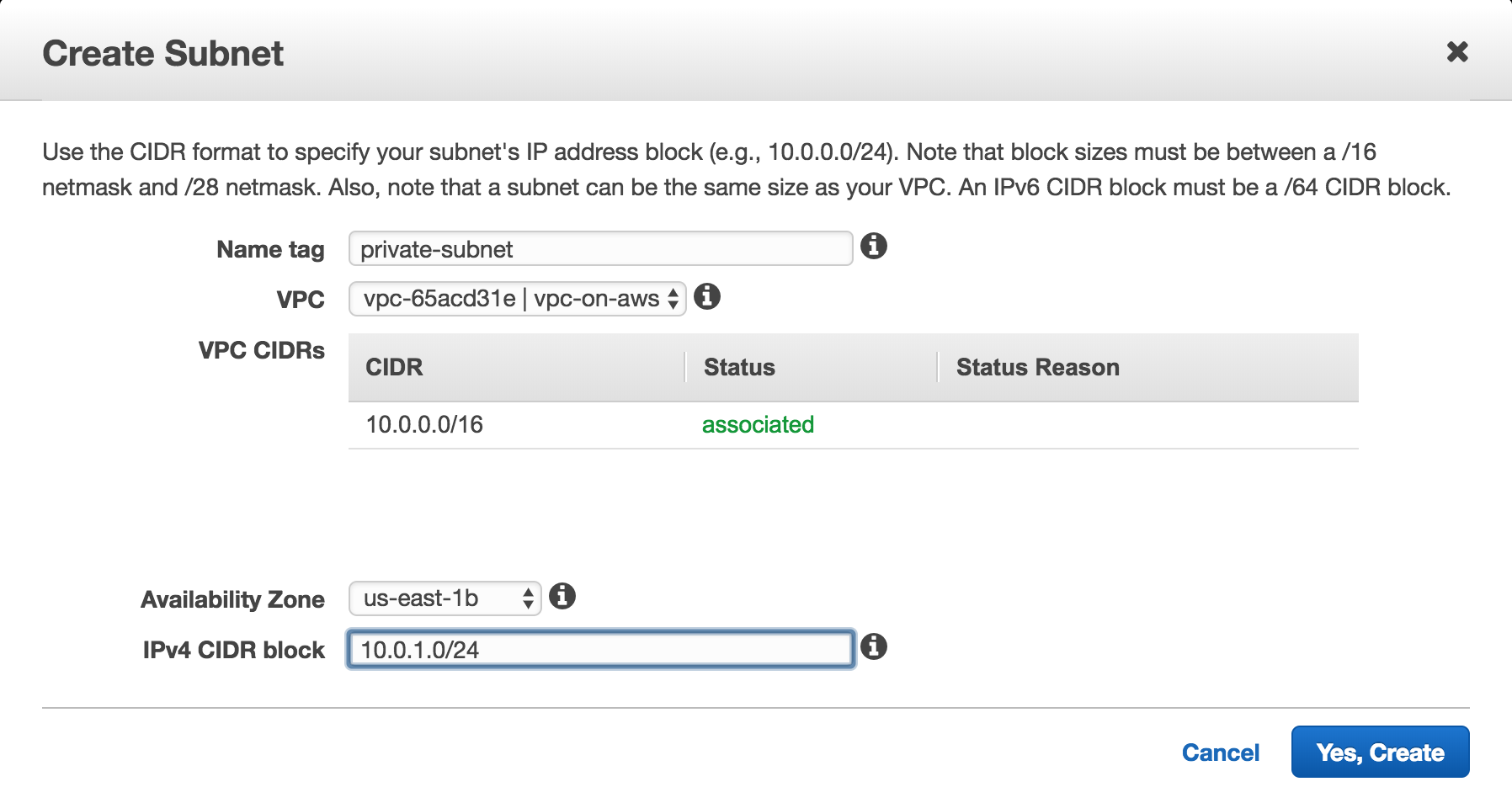
- Got to
Subnets - Click
Create subnetfor creating public subnets
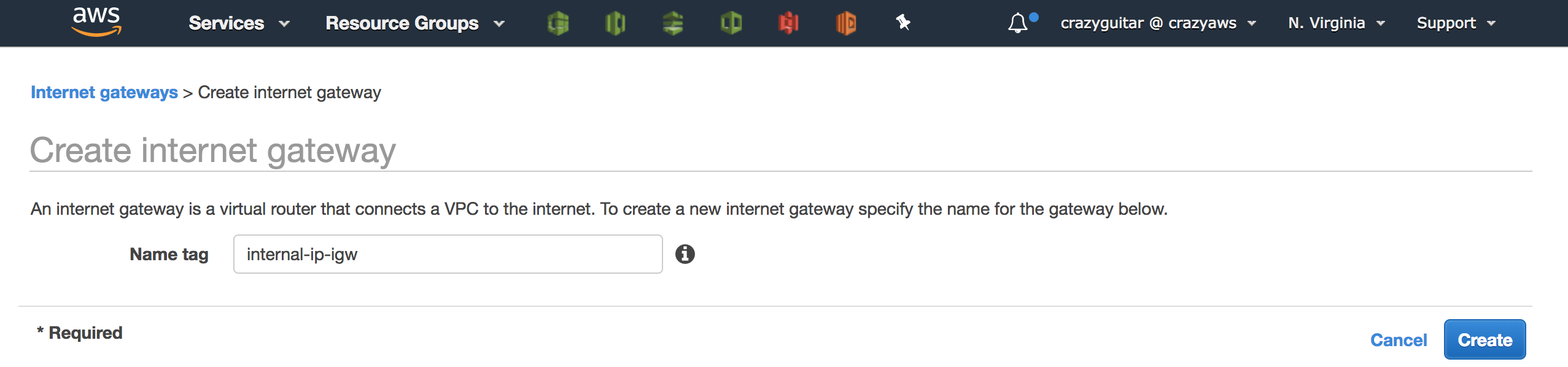
- Go to
Internal Gatewaysand clickCreate internal gateway
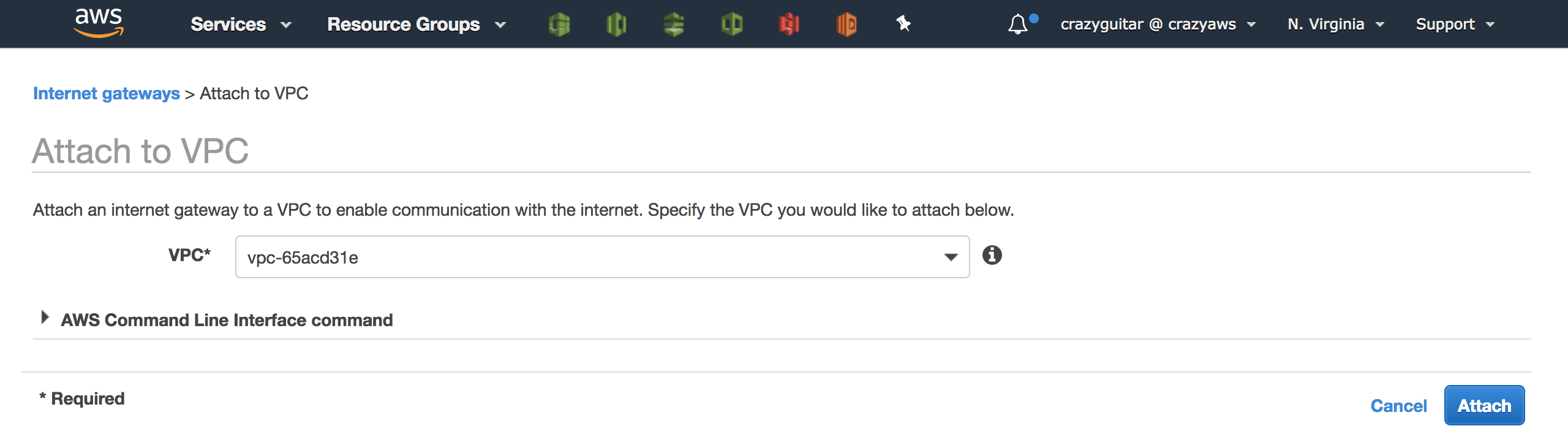
- Attach to VPC
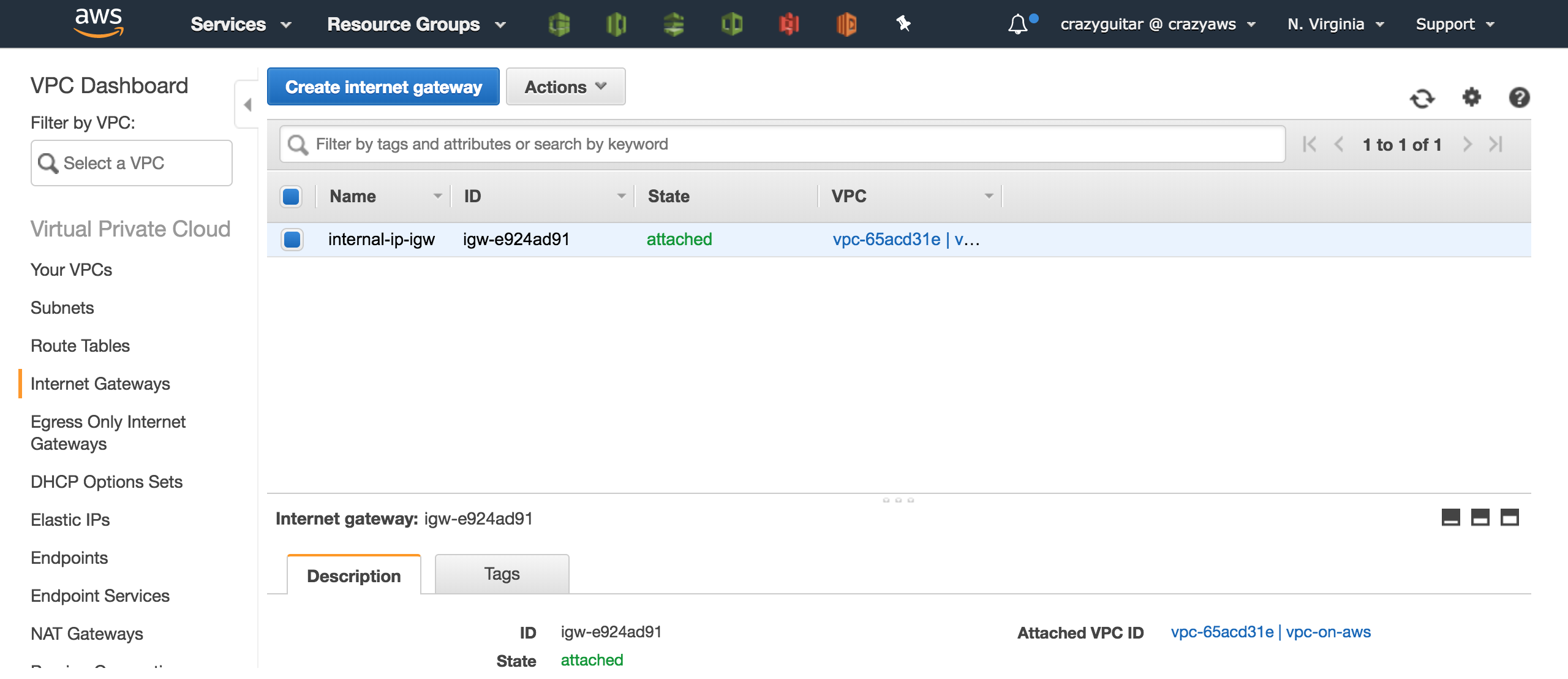
- Check the result of attachment
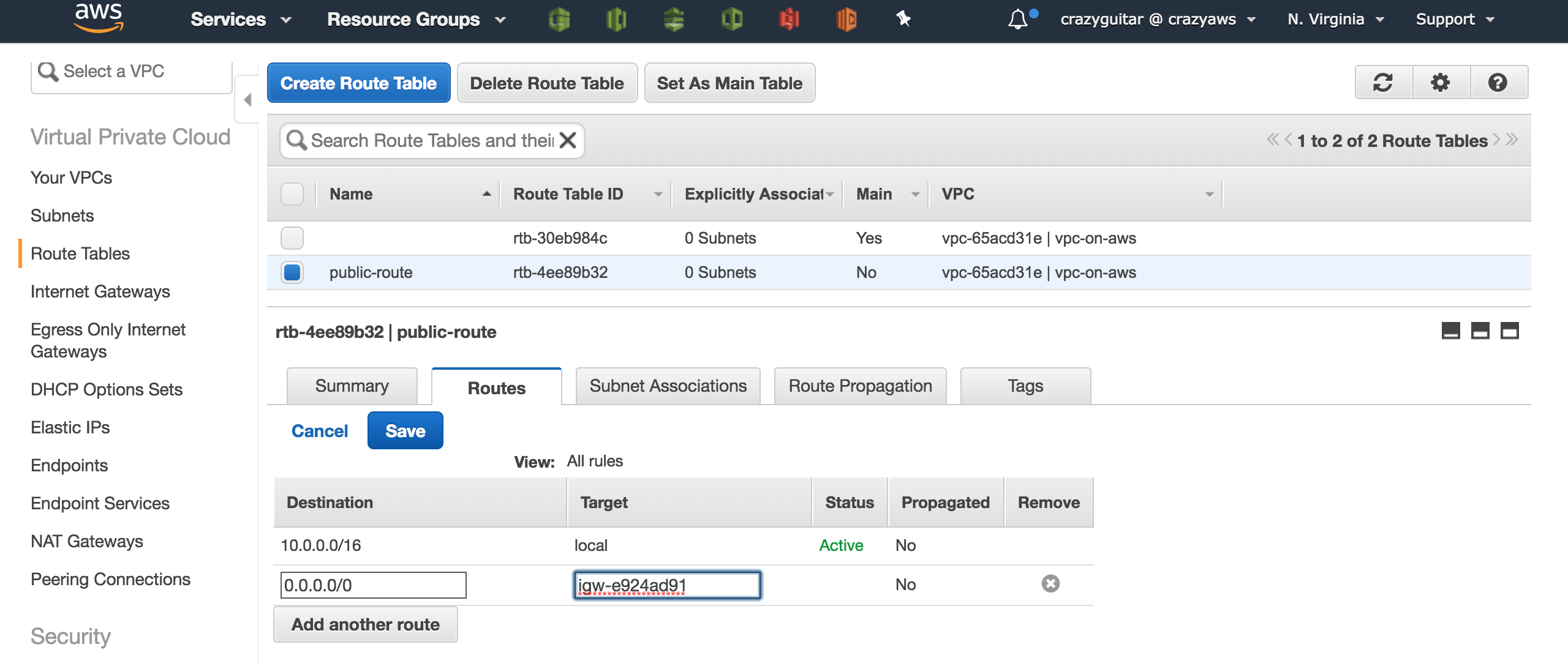
- Click
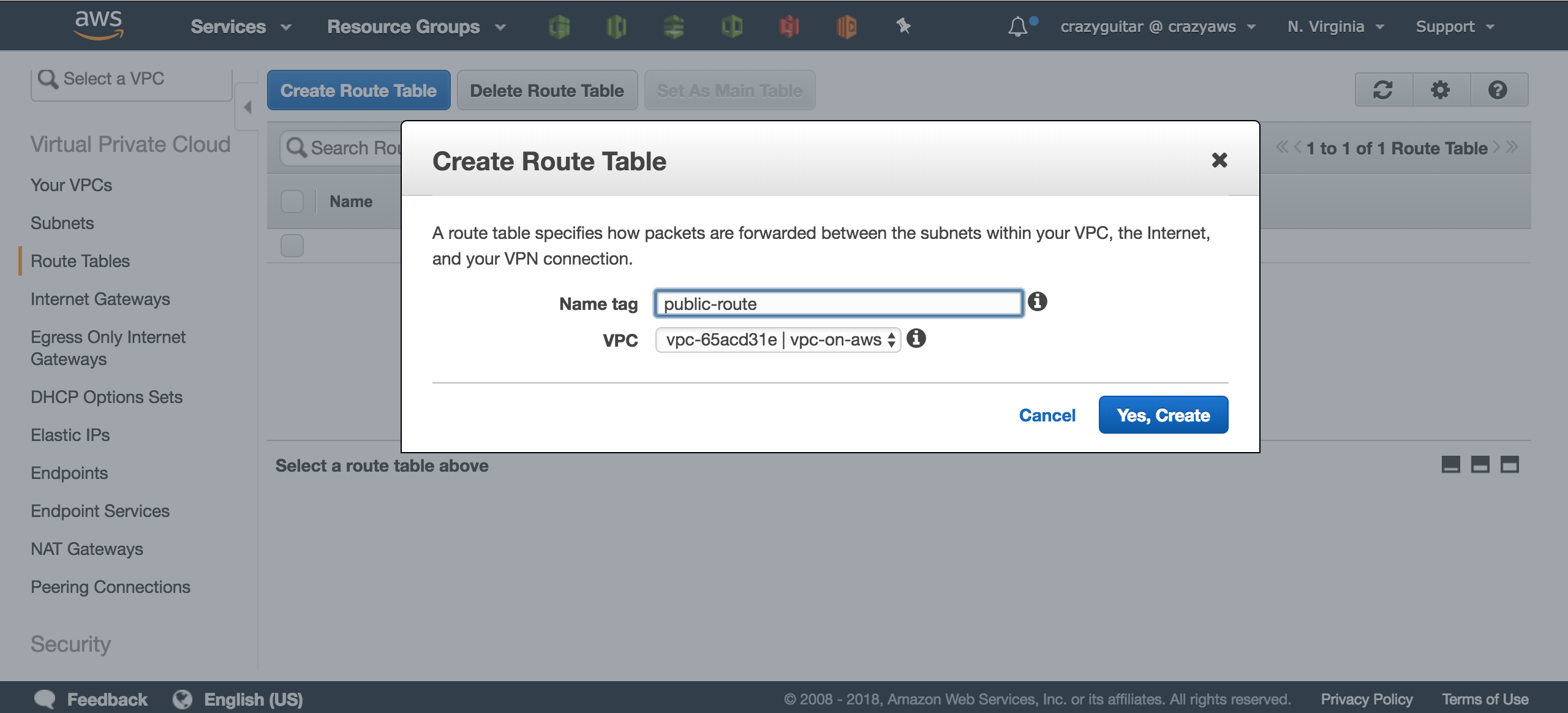
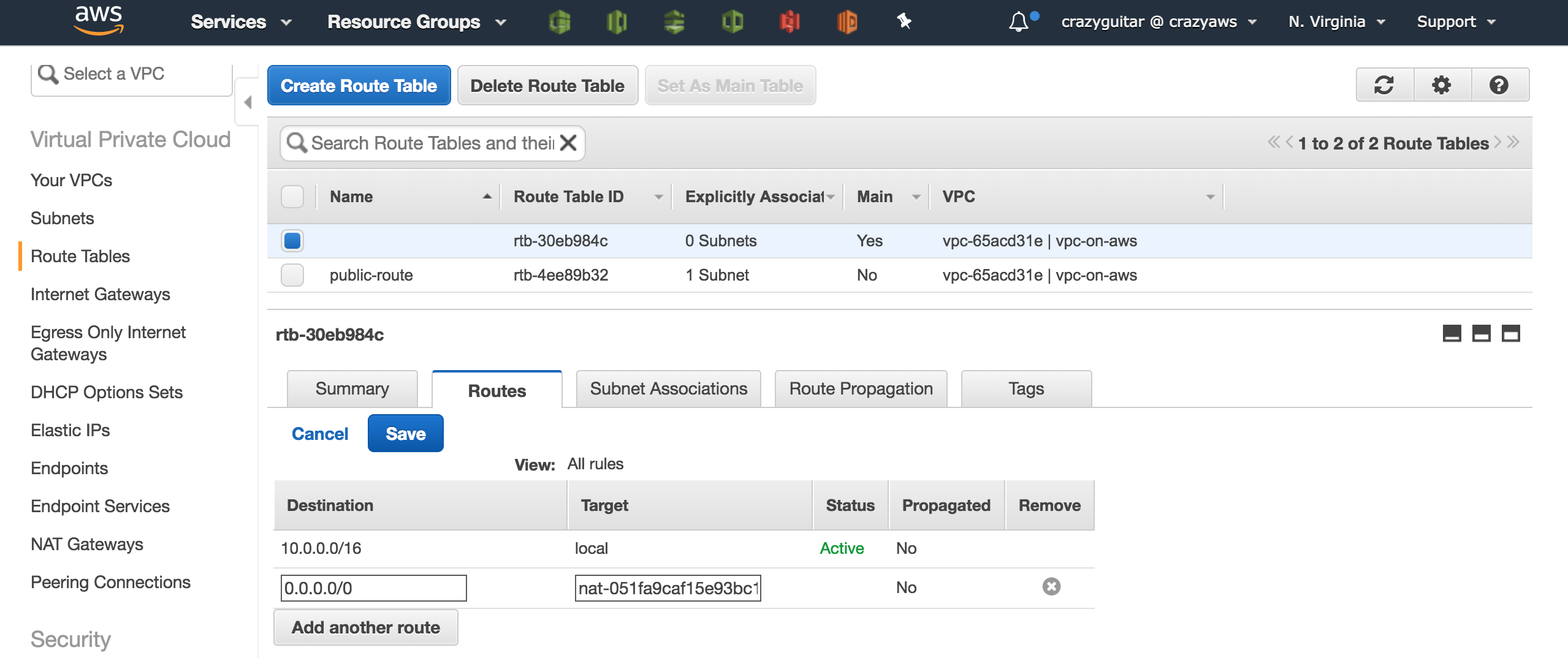
Route Tables - Click
Create Route Table
- Add a routing rule in route table
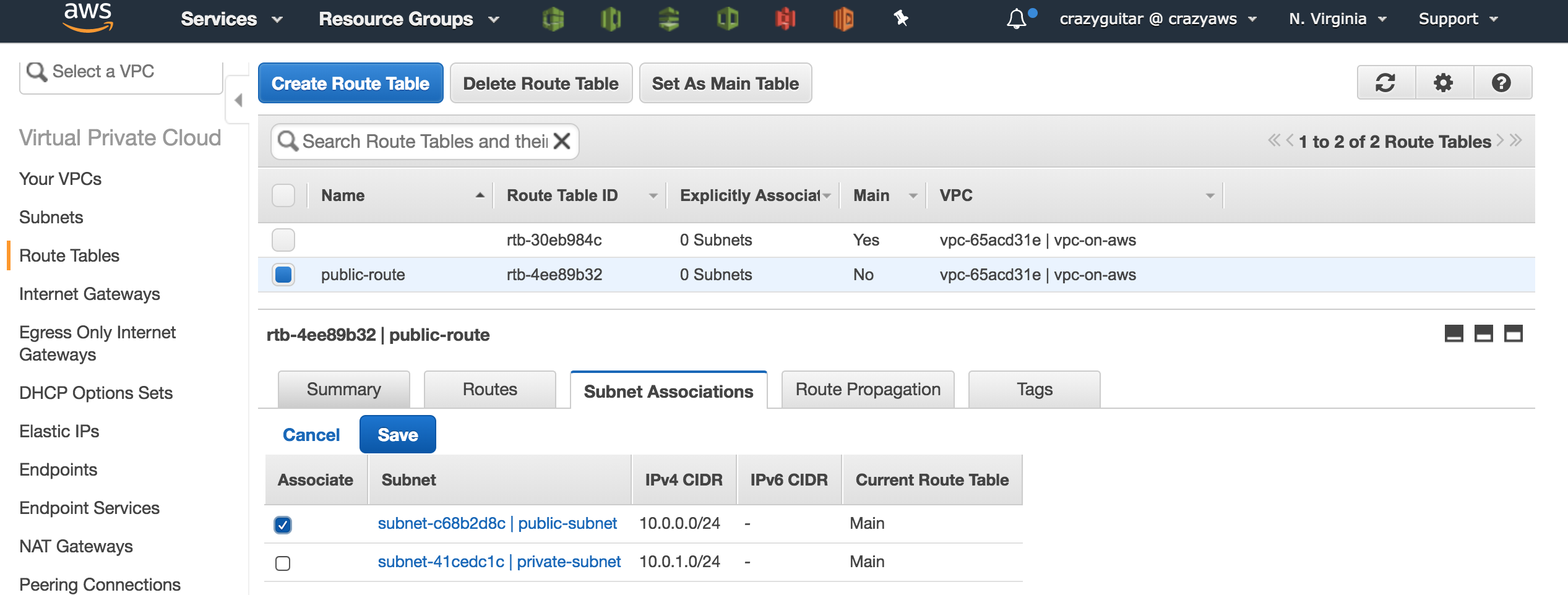
- Click
Subnet Associationstab and associate to public subnet
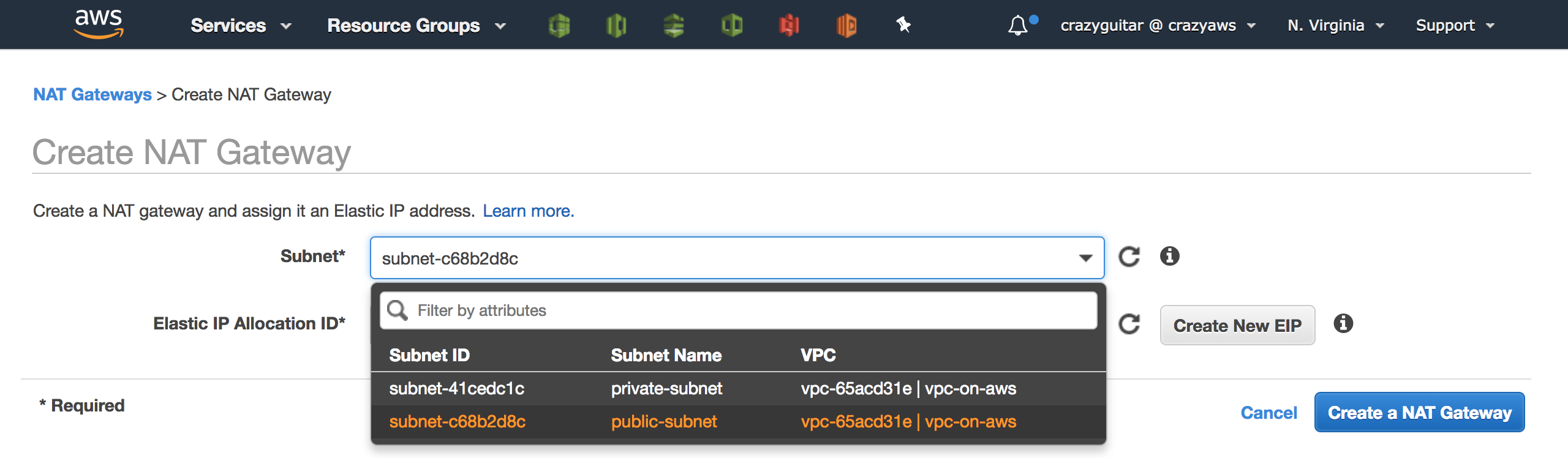
- Go to
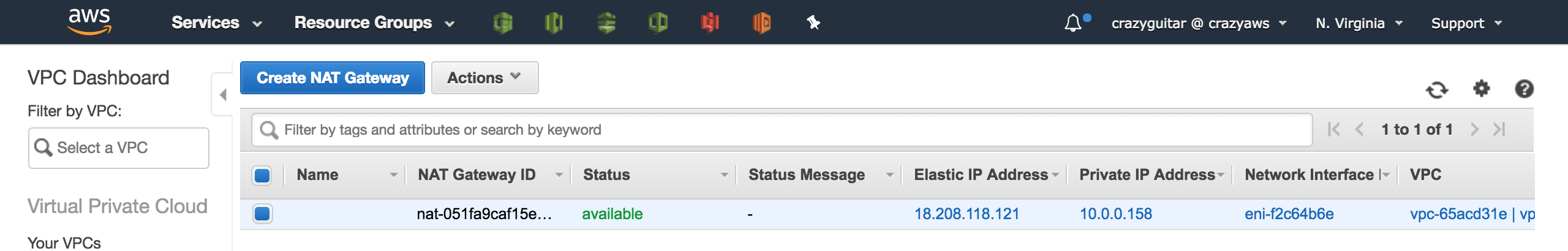
NAT Gateways - Click
Create NAT Gateway
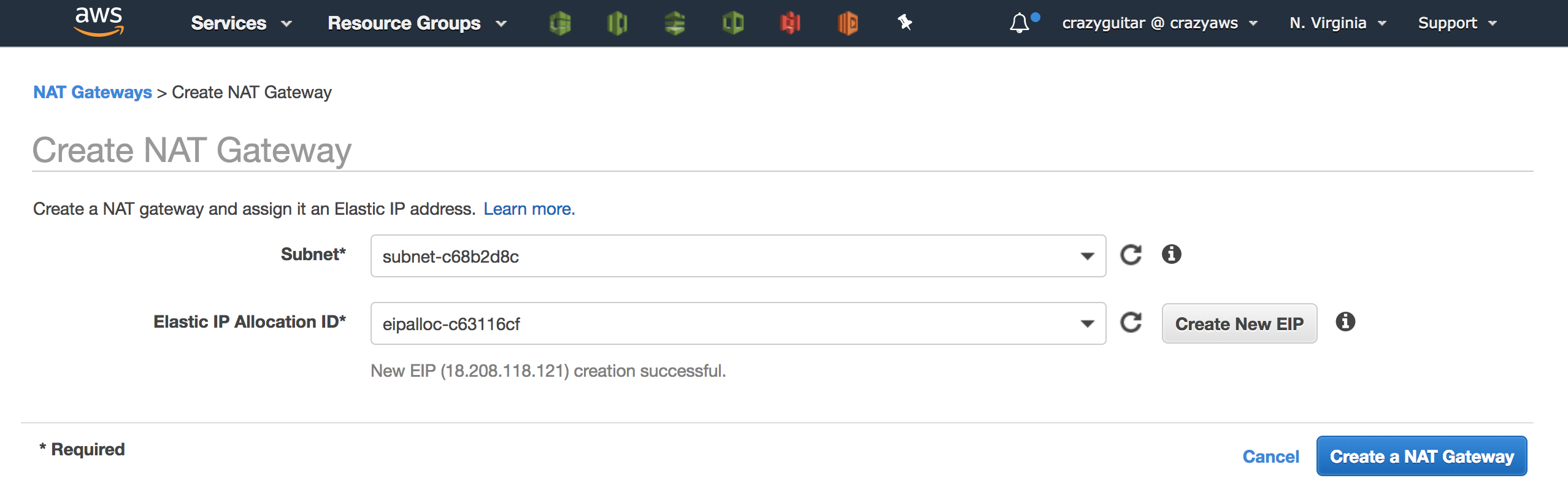
- Create a EIP
- Edit the main route table
const express = require('express');
const app = express();
app.get('/', function(req, res){
const ip = req.headers['x-real-ip'] || req.connection.remoteAddress;
console.log(ip);
res.send("Hello world!");
});
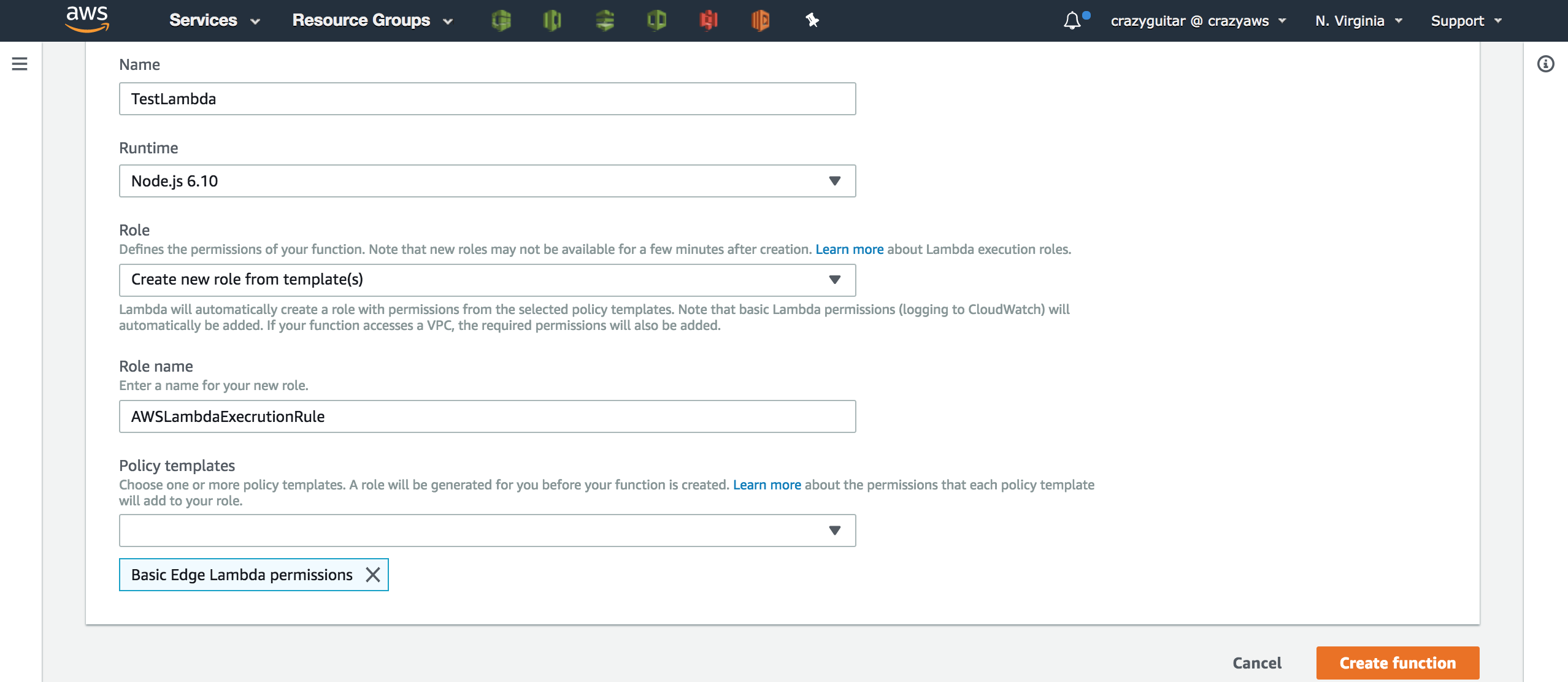
app.listen(3000);- Create a lambda function on AWS
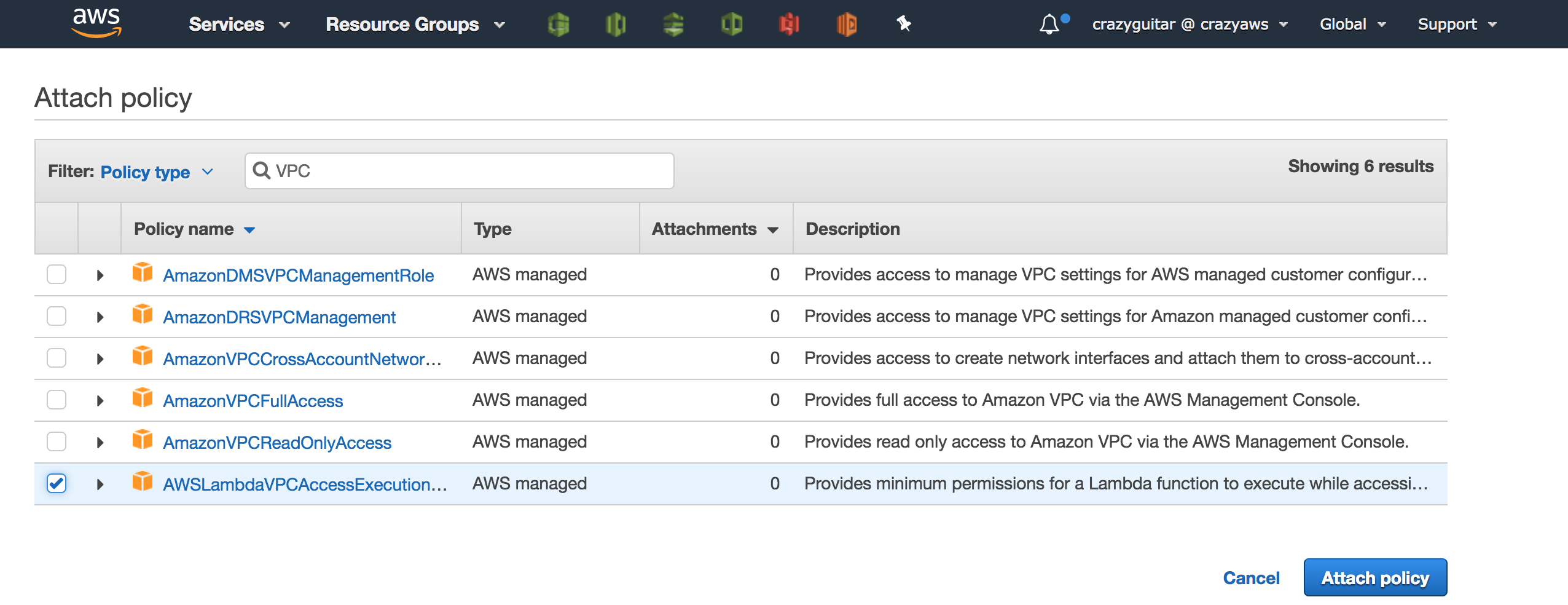
- Go to IAM and assign a VPC permission to execturion role
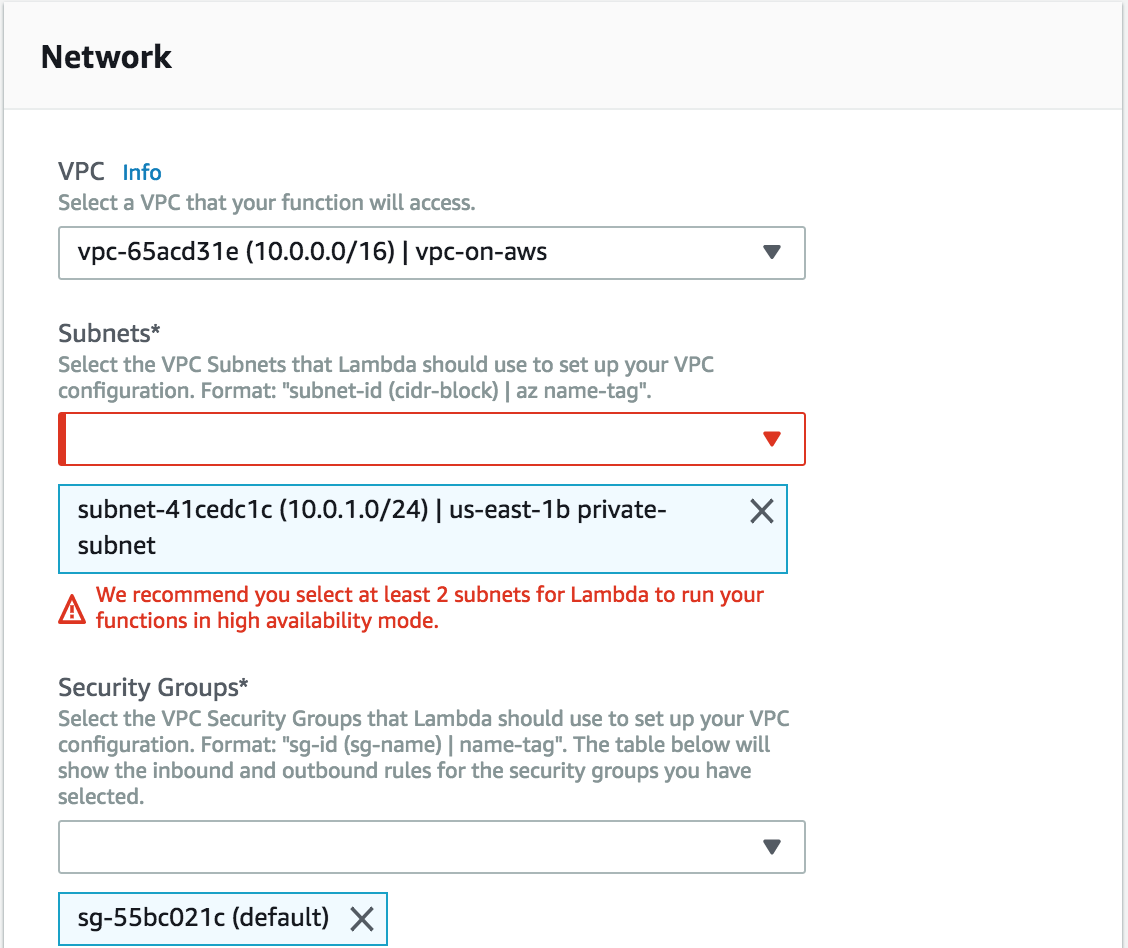
- Attach VPC to lambda
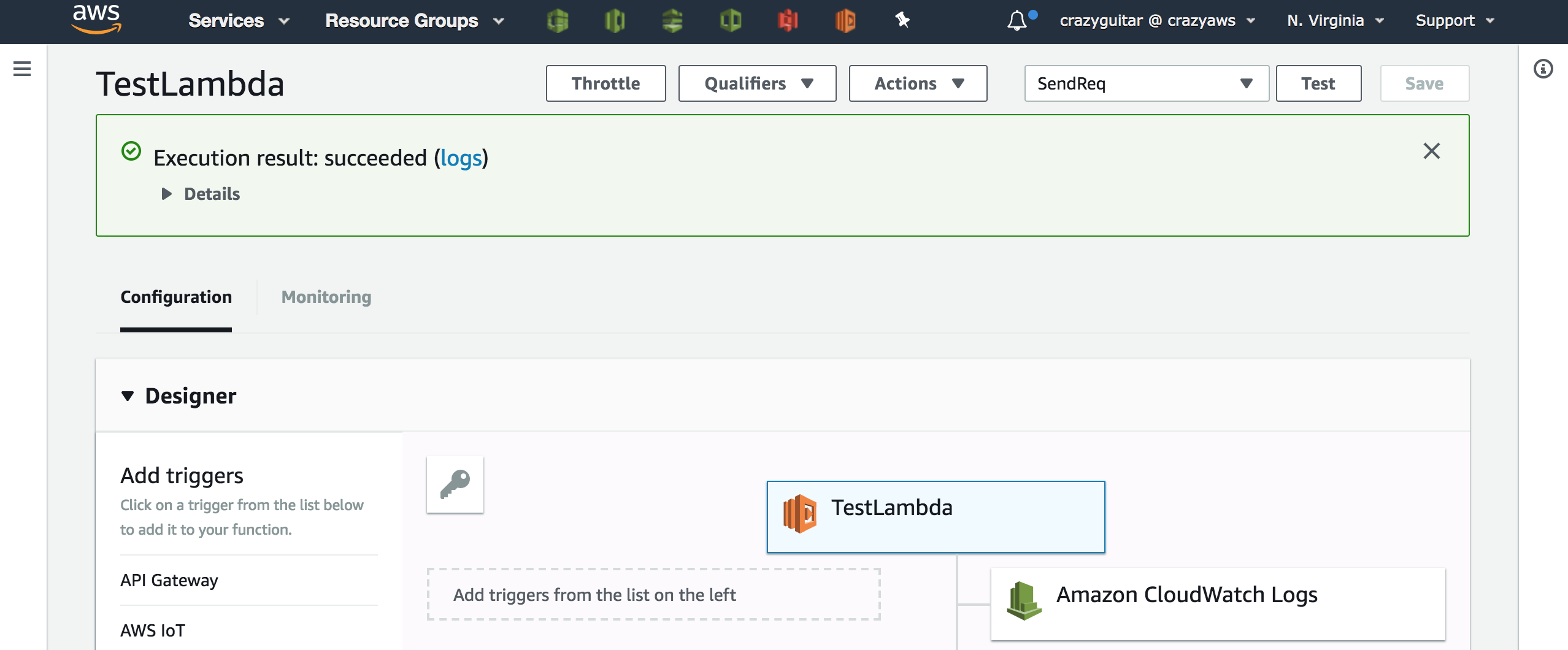
- Test sending a request to server
- Check execution result
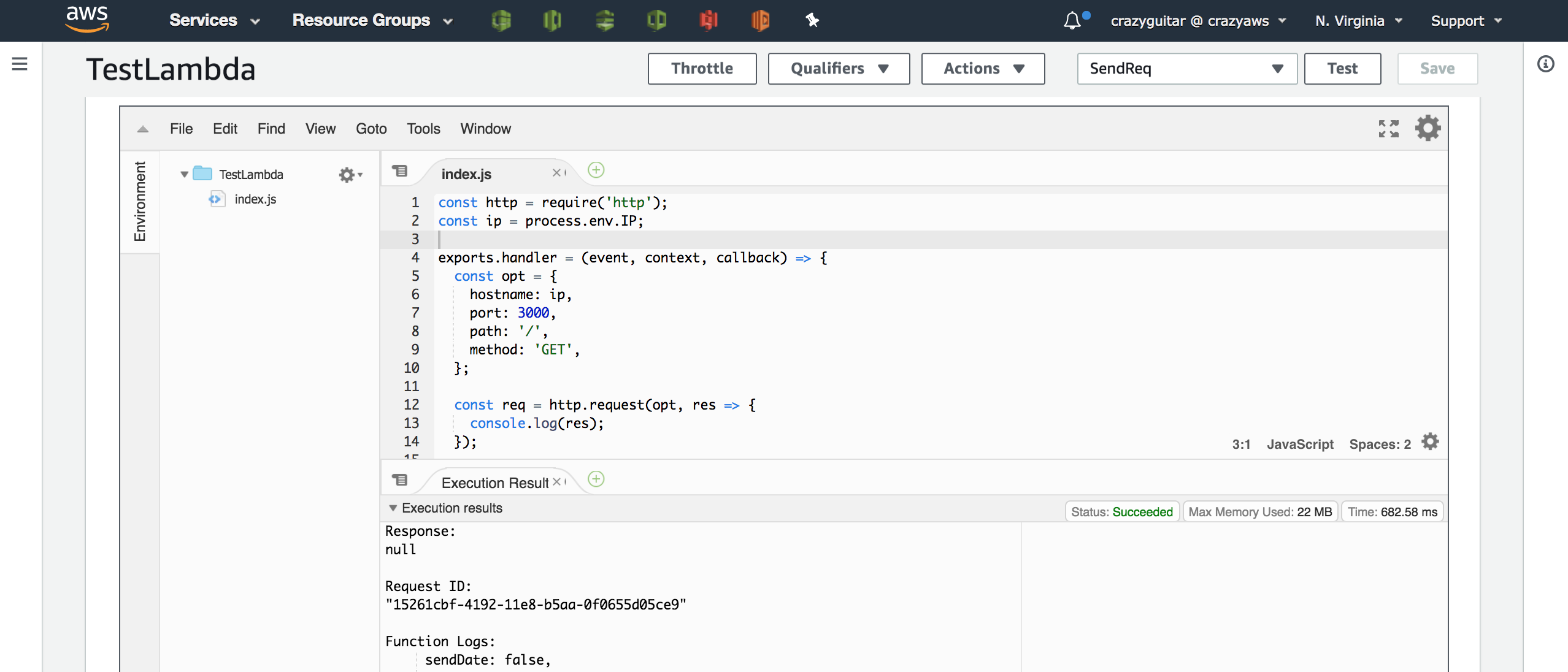
const http = require('http');
const ip = process.env.IP;
exports.handler = (event, context, callback) => {
const opt = {
hostname: ip,
port: 3000,
path: '/',
method: 'GET',
};
const req = http.request(opt, res => {
console.log(res);
});
req.end();
};- Check server output and EIP
output:
$ node app.js
::ffff:18.208.118.121