Last active
July 15, 2020 18:36
-
-
Save darkpixel/549237f9ab8de57165d76762304a530a to your computer and use it in GitHub Desktop.
PDQ Inventory collections for detecting CVE-2020-1350 DNS vulnerability
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="utf-8"?> | |
| <AdminArsenal.Export Code="PDQInventory" Name="PDQ Inventory" Version="19.0.40.0" MinimumVersion="4.0"> | |
| <Collection> | |
| <ReportDefinition name="Definition"> | |
| <RootFilter name="Filter"> | |
| <Comparison>All</Comparison> | |
| <Filters type="list"> | |
| <ValueFilter> | |
| <Table>Service</Table> | |
| <Column>Name</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>dns</Value> | |
| </ValueFilter> | |
| </Filters> | |
| </RootFilter> | |
| <ReportDefinitionTypeName>BasicReportDefinition</ReportDefinitionTypeName> | |
| <Columns type="list"> | |
| <Column> | |
| <Column>ComputerId</Column> | |
| <Summary></Summary> | |
| <Table>Computer</Table> | |
| <Title></Title> | |
| </Column> | |
| </Columns> | |
| </ReportDefinition> | |
| <IsDrilldown value="true" /> | |
| <ImportedPath></ImportedPath> | |
| <TypeName>DynamicCollection</TypeName> | |
| <Created>2020-07-15T08:16:03.0000000-07:00</Created> | |
| <Description></Description> | |
| <Error></Error> | |
| <Id value="1310" /> | |
| <IsEnabled value="true" /> | |
| <Modified>2020-07-15T08:16:20.0000000-07:00</Modified> | |
| <Name>DNS Servers</Name> | |
| <ParentId value="null" /> | |
| <Path>DNS Servers</Path> | |
| <Type>DynamicCollection</Type> | |
| <Children type="list"> | |
| <Collection> | |
| <ReportDefinition name="Definition"> | |
| <RootFilter name="Filter"> | |
| <Comparison>Any</Comparison> | |
| <Filters type="list"> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4558998</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565483</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565503</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565511</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565524</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565529</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565535</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565536</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565537</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565539</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565540</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565541</Value> | |
| </ValueFilter> | |
| </Filters> | |
| </RootFilter> | |
| <ReportDefinitionTypeName>BasicReportDefinition</ReportDefinitionTypeName> | |
| <Columns type="list"> | |
| <Column> | |
| <Column>ComputerId</Column> | |
| <Summary></Summary> | |
| <Table>Computer</Table> | |
| <Title></Title> | |
| </Column> | |
| </Columns> | |
| </ReportDefinition> | |
| <IsDrilldown value="true" /> | |
| <ImportedPath></ImportedPath> | |
| <TypeName>DynamicCollection</TypeName> | |
| <Created>2020-07-15T08:16:04.0000000-07:00</Created> | |
| <Description></Description> | |
| <Error></Error> | |
| <Id value="1312" /> | |
| <IsEnabled value="true" /> | |
| <Modified>2020-07-15T08:19:16.0000000-07:00</Modified> | |
| <Name>CVE-2020-1350 Patched</Name> | |
| <ParentId value="1310" /> | |
| <Path>DNS Servers\CVE-2020-1350 Patched</Path> | |
| <Type>DynamicCollection</Type> | |
| <Children type="list" /> | |
| </Collection> | |
| <Collection> | |
| <ReportDefinition name="Definition"> | |
| <RootFilter name="Filter"> | |
| <Comparison>All</Comparison> | |
| <Filters type="list"> | |
| <GroupFilter> | |
| <Comparison>NotAny</Comparison> | |
| <Filters type="list"> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4558998</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565483</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565503</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565511</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565524</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565529</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565535</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565536</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565537</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565539</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565540</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>HotFix</Table> | |
| <TableTitle>Hot Fix</TableTitle> | |
| <Column>Name</Column> | |
| <Comparison>Contains</Comparison> | |
| <Value>KB4565541</Value> | |
| </ValueFilter> | |
| </Filters> | |
| </GroupFilter> | |
| <GroupFilter> | |
| <Comparison>NotAll</Comparison> | |
| <Filters type="list"> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Hive</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>HKEY_LOCAL_MACHINE</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>PathName</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>SYSTEM\CurrentControlSet\Services\DNS\Parameters</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Name</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>TcpReceivePacketSize</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Value</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>65280</Value> | |
| </ValueFilter> | |
| </Filters> | |
| </GroupFilter> | |
| </Filters> | |
| </RootFilter> | |
| <ReportDefinitionTypeName>BasicReportDefinition</ReportDefinitionTypeName> | |
| <Columns type="list"> | |
| <Column> | |
| <Column>ComputerId</Column> | |
| <Summary></Summary> | |
| <Table>Computer</Table> | |
| <Title></Title> | |
| </Column> | |
| </Columns> | |
| </ReportDefinition> | |
| <IsDrilldown value="true" /> | |
| <ImportedPath></ImportedPath> | |
| <TypeName>DynamicCollection</TypeName> | |
| <Created>2020-07-15T08:16:04.0000000-07:00</Created> | |
| <Description></Description> | |
| <Error></Error> | |
| <Id value="1313" /> | |
| <IsEnabled value="true" /> | |
| <Modified>2020-07-15T08:25:00.0000000-07:00</Modified> | |
| <Name>CVE-2020-1350 Vulnerable</Name> | |
| <ParentId value="1310" /> | |
| <Path>DNS Servers\CVE-2020-1350 Vulnerable</Path> | |
| <Type>DynamicCollection</Type> | |
| <Children type="list" /> | |
| </Collection> | |
| <Collection> | |
| <ReportDefinition name="Definition"> | |
| <RootFilter name="Filter"> | |
| <Comparison>All</Comparison> | |
| <Filters type="list"> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Hive</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>HKEY_LOCAL_MACHINE</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>PathName</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>SYSTEM\CurrentControlSet\Services\DNS\Parameters</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Name</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>TcpReceivePacketSize</Value> | |
| </ValueFilter> | |
| <ValueFilter> | |
| <Table>Registry</Table> | |
| <Column>Value</Column> | |
| <Comparison>Equals</Comparison> | |
| <Value>65280</Value> | |
| </ValueFilter> | |
| </Filters> | |
| </RootFilter> | |
| <ReportDefinitionTypeName>BasicReportDefinition</ReportDefinitionTypeName> | |
| <Columns type="list"> | |
| <Column> | |
| <Column>ComputerId</Column> | |
| <Summary></Summary> | |
| <Table>Computer</Table> | |
| <Title></Title> | |
| </Column> | |
| </Columns> | |
| </ReportDefinition> | |
| <IsDrilldown value="true" /> | |
| <ImportedPath></ImportedPath> | |
| <TypeName>DynamicCollection</TypeName> | |
| <Created>2020-07-15T08:16:04.0000000-07:00</Created> | |
| <Description></Description> | |
| <Error></Error> | |
| <Id value="1314" /> | |
| <IsEnabled value="true" /> | |
| <Modified>2020-07-15T08:16:04.0000000-07:00</Modified> | |
| <Name>CVE-2020-1350 Remediated</Name> | |
| <ParentId value="1310" /> | |
| <Path>DNS Servers\CVE-2020-1350 Remediated</Path> | |
| <Type>DynamicCollection</Type> | |
| <Children type="list" /> | |
| </Collection> | |
| </Children> | |
| </Collection> | |
| </AdminArsenal.Export> |
Author
Working well thank you! Pulled the new collections under an already predefined Servers Dynamic collection. Just need to create another dynamic collection to see if the DNS Server role is added.. any ideas how to do this?
Author
@TiggBloomz I updated the gist to include a top-level collection called "DNS Servers" that identifies if the DNS service exists and then has sub collections for "Patched", "Remediated", and "Not Fixed".
Author
Author
I also created a PDQ Deploy package to remediate the issue via the Registry fix: https://gist.github.com/darkpixel/f638b1827b41b4e530a86854223f70fa
Author
Removed accidentally included collection for detecting GSPS
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
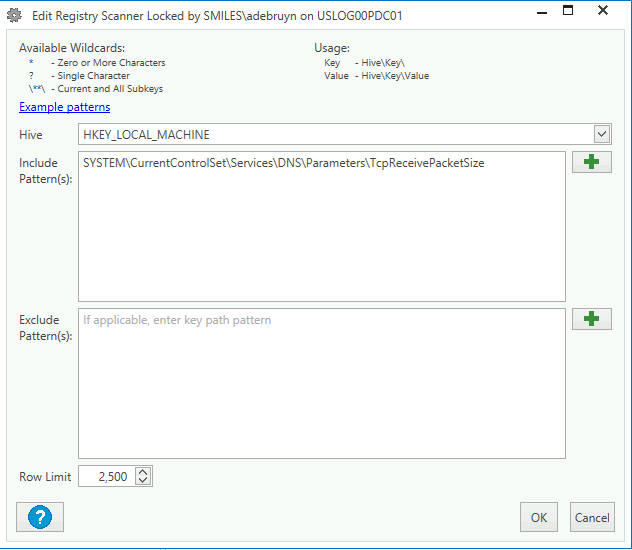
This will provide you with two collections to determine if computers have the patch installed or not.
I recommend creating a "top-level" collection that filters your computers into "servers" as well as detecting if the DNS server service (or role) is installed, then import these two collections under that collection. Feedback welcome.