- https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-overview#communicate-between-azure-resources
- https://docs.microsoft.com/en-us/azure/virtual-network/vnet-integration-for-azure-services
Some Azure PaaS services can be deployed into VNet and then they are usable through Azure VNet services and on-prem when using Express Route or VPN with proper routing setup.
- https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-for-azure-services
- Usually expensive tier of service required. Some examples:
- Logic apps: ISE: 0.95(developer tier) - 5.92(premium tier) €/h on top of normal operating cost
- API management: requires Developer or premium tier: https://azure.microsoft.com/en-us/pricing/details/api-management/
- Some services requires delegated subnet. E.g. ACI creates delegation automatically if needed.
- only one type of delegation supported per subnet
- some services requires also dedicated subnet
- Unsupported services:
- Azure Data Factory Integration runtime
- (2021-04-05) On preview only. Current documentation suggests installing SHIR into Azure VM
- Preview is using private link to connect Azure Data resources
- TBD
- Azure Data Factory Integration runtime
Short description:
-
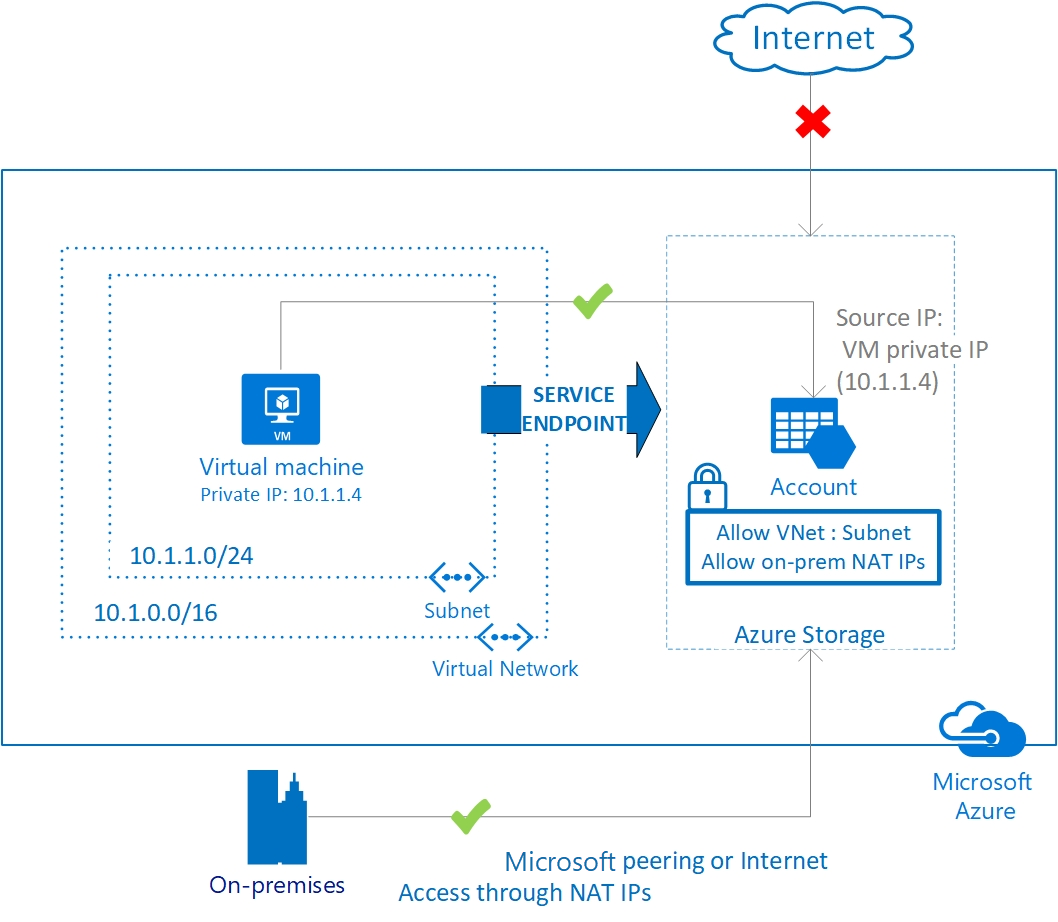
Accessing the service using public endpoints by extending a virtual network to the service, through service endpoints. Service endpoints allow service resources to be secured to the virtual network.
- Allows direct access from VNet to resource
- Rewrites source IP and internally uses BGP to change routing from public resource IP to internal VNet faced IP
Usable e.g. to connect from VM to SQL or Storage Account without passing data through internet
- Does not support routing
- VNet peering support?
- The image describing on-prem access is whitelisting Express route public address or on-prem NAT gateway address
- Express route != public internet
- For on-prem traffic will go through public internet
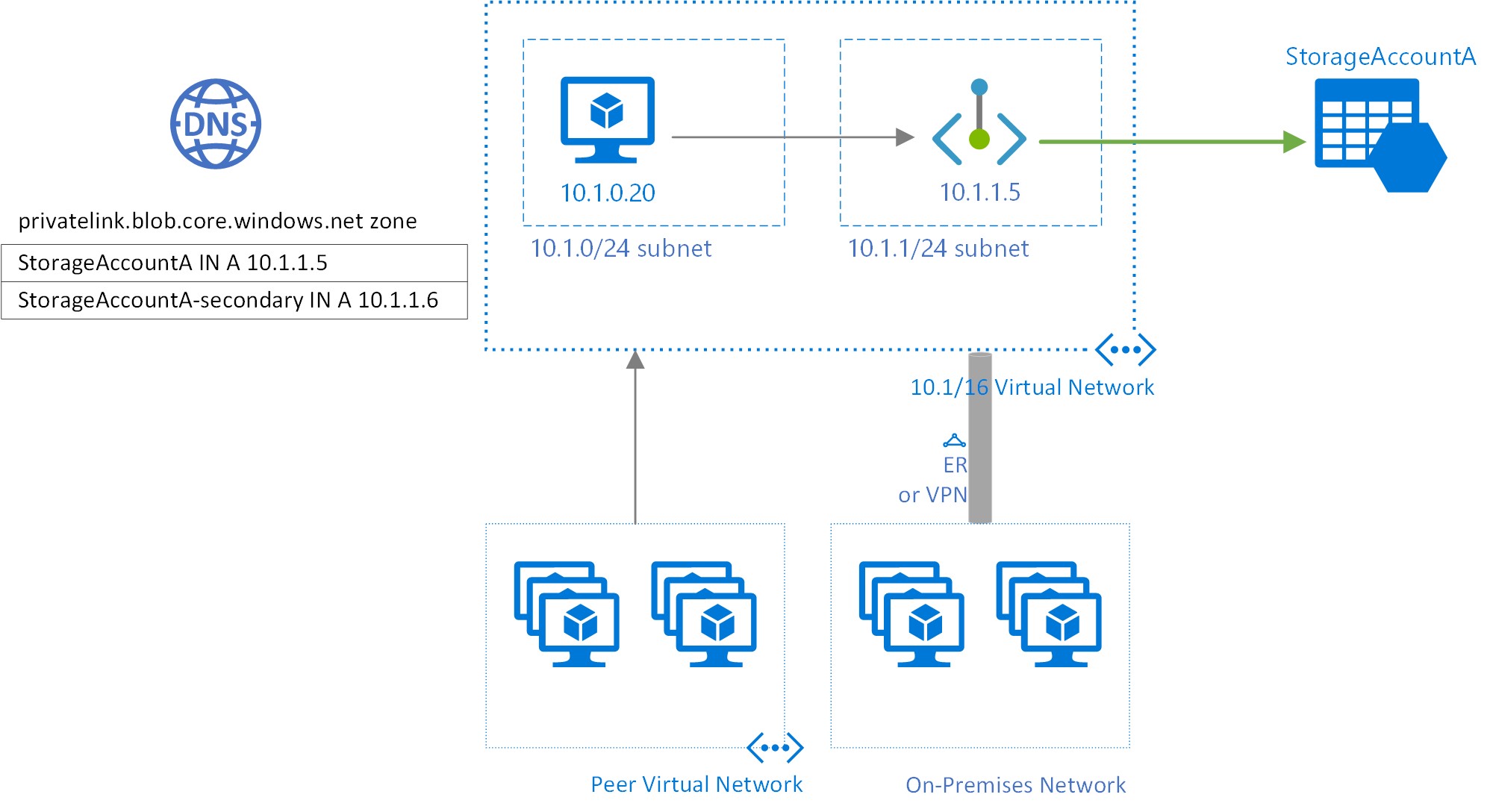
Private endpoint is transparent connection from Azure Vnet IP to Azure service.
-
https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-overview
-
https://docs.microsoft.com/en-us/azure/storage/common/storage-private-endpoints
- Conceptual image when used with storage accounts
-
Private endpoint and configured VNet must reside on the same Azure region and tenant
-
The target resource can be in the foreign Azure tenant
-
Authorization process if private endpoint is linked to external resource
-
Remember to check resource specific documentation for more information or limitations
-
https://journeyofthegeek.com/2020/03/05/azure-private-link-and-dns-part-1/
-
https://journeyofthegeek.com/2020/03/06/azure-private-link-and-dns-part-2/
-
https://bloggerz.cloud/2020/12/18/azure-private-link-and-dns/
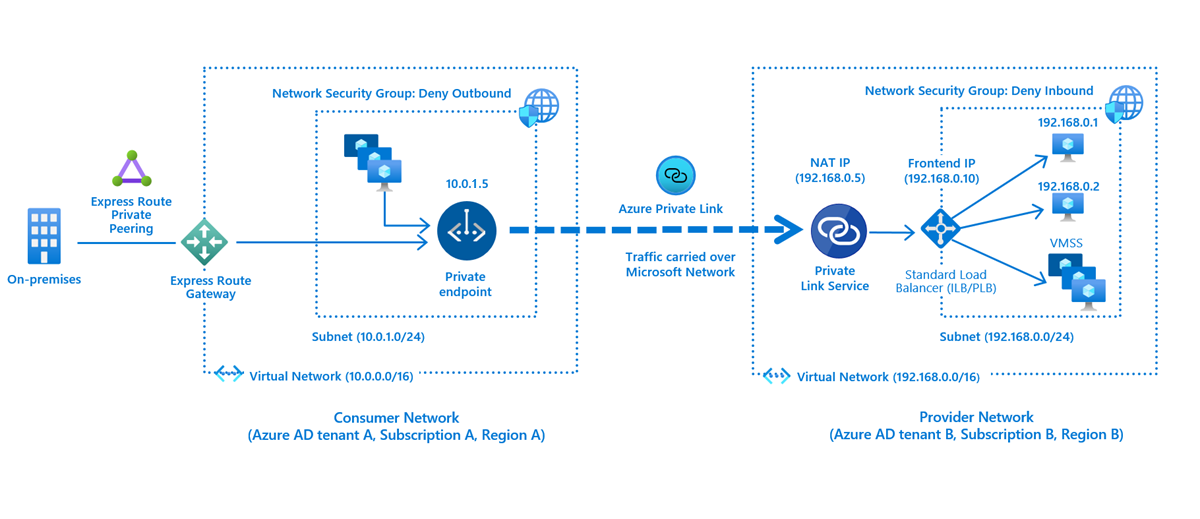
Azure Private Link service is the reference to your own service that is powered by Azure Private Link. Your service that is running behind Azure Standard Load Balancer can be enabled for Private Link access so that consumers to your service can access it privately from their own VNets.
Private link is a service which can be used as facade that converts your own services to be interacted with private endpoints. In this case the service that is bound with private endpoint is private link. See image on the overview article.