-
Star
(606)
You must be signed in to star a gist -
Fork
(151)
You must be signed in to fork a gist
-
-
Save mackwage/08604751462126599d7e52f233490efe to your computer and use it in GitHub Desktop.
| :: Windows 10 Hardening Script | |
| :: This is based mostly on my own personal research and testing. My objective is to secure/harden Windows 10 as much as possible while not impacting usability at all. (Think being able to run on this computer's of family members so secure them but not increase the chances of them having to call you to troubleshoot something related to it later on). References for virtually all settings can be found at the bottom. Just before the references section, you will always find several security settings commented out as they could lead to compatibility issues in common consumer setups but they're worth considering. | |
| :: Obligatory 'views are my own'. :) | |
| :: Thank you @jaredhaight for the Win Firewall config recommendations! | |
| :: Thank you @ricardojba for the DLL Safe Order Search reg key! | |
| :: Thank you @jessicaknotts for the help on testing Exploit Guard configs and checking privacy settings! | |
| :: Best script I've found for Debloating Windows 10: https://github.com/Sycnex/Windows10Debloater | |
| :: | |
| ::####################################################################### | |
| :: | |
| :: Change file associations to protect against common ransomware attacks | |
| :: Note that if you legitimately use these extensions, like .bat, you will now need to execute them manually from cmd or powershel | |
| :: Alternatively, you can right-click on them and hit 'Run as Administrator' but ensure it's a script you want to run :) | |
| :: https://support.microsoft.com/en-us/help/883260/information-about-the-attachment-manager-in-microsoft-windows | |
| :: --------------------- | |
| ftype htafile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype wshfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype wsffile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype batfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype jsfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype jsefile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype vbefile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| ftype vbsfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1" | |
| :: | |
| ::####################################################################### | |
| :: Enable and configure Windows Defender and advanced settings | |
| ::####################################################################### | |
| :: | |
| :: Reset Defender to defaults. Commented out but available for reference | |
| ::"%programfiles%"\"Windows Defender"\MpCmdRun.exe -RestoreDefaults | |
| :: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#defender-submitsamplesconsent | |
| :: https://docs.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=win10-ps | |
| :: | |
| :: Start Defender Service | |
| sc start WinDefend | |
| ::Enable Windows Defender sandboxing | |
| setx /M MP_FORCE_USE_SANDBOX 1 | |
| :: Update signatures | |
| "%ProgramFiles%"\"Windows Defender"\MpCmdRun.exe -SignatureUpdate | |
| :: Enable Defender signatures for Potentially Unwanted Applications (PUA) | |
| powershell.exe Set-MpPreference -PUAProtection enable | |
| :: Enable Defender periodic scanning | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows Defender" /v PassiveMode /t REG_DWORD /d 2 /f | |
| :: Enable Cloud functionality of Windows Defender | |
| powershell.exe Set-MpPreference -MAPSReporting Advanced | |
| powershell.exe Set-MpPreference -SubmitSamplesConsent 0 | |
| :: | |
| :: Enable early launch antimalware driver for scan of boot-start drivers | |
| :: 3 is the default which allows good, unknown and 'bad but critical'. Recommend trying 1 for 'good and unknown' or 8 which is 'good only' | |
| reg add "HKCU\SYSTEM\CurrentControlSet\Policies\EarlyLaunch" /v DriverLoadPolicy /t REG_DWORD /d 3 /f | |
| :: | |
| :: Enable ASR rules in Win10 1903 ExploitGuard to mitigate Office malspam | |
| :: Blocks Office childprocs, Office proc injection, Office win32 api calls & executable content creation | |
| :: Note these only work when Defender is your primary AV | |
| :: | |
| :: Block Office Child Process Creation | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids D4F940AB-401B-4EFC-AADC-AD5F3C50688A -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block Process Injection | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84 -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block Win32 API calls in macros | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block Office from creating executables | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 3B576869-A4EC-4529-8536-B80A7769E899 -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block execution of potentially obfuscated scripts | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block executable content from email client and webmail | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block JavaScript or VBScript from launching downloaded executable content | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids D3E037E1-3EB8-44C8-A917-57927947596D -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block lsass cred theft | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2 -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block untrusted and unsigned processes that run from USB | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4 -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block Adobe Reader from creating child processes | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block persistence through WMI event subscription | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids e6db77e5-3df2-4cf1-b95a-636979351e5b -AttackSurfaceReductionRules_Actions Enabled | |
| :: Block process creations originating from PSExec and WMI commands | |
| powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids d1e49aac-8f56-4280-b9ba-993a6d77406c -AttackSurfaceReductionRules_Actions Enabled | |
| :: | |
| :: Enable Defender exploit system-wide protection | |
| :: The commented line includes CFG which can cause issues with apps like Discord & Mouse Without Borders | |
| :: powershell.exe Set-Processmitigation -System -Enable DEP,EmulateAtlThunks,BottomUp,HighEntropy,SEHOP,SEHOPTelemetry,TerminateOnError,CFG | |
| powershell.exe Set-Processmitigation -System -Enable DEP,EmulateAtlThunks,BottomUp,HighEntropy,SEHOP,SEHOPTelemetry,TerminateOnError | |
| :: | |
| ::####################################################################### | |
| :: Enable and Configure Internet Browser Settings | |
| ::####################################################################### | |
| :: | |
| :: Enable SmartScreen for Edge | |
| reg add "HKCU\SOFTWARE\Policies\Microsoft\MicrosoftEdge\PhishingFilter" /v EnabledV9 /t REG_DWORD /d 1 /f | |
| :: Enable Notifications in IE when a site attempts to install software | |
| reg add "HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer" /v SafeForScripting /t REG_DWORD /d 0 /f | |
| :: Disable Edge password manager to encourage use of proper password manager | |
| reg add "HKCU\SOFTWARE\Policies\Microsoft\MicrosoftEdge\Main" /v "FormSuggest Passwords" /t REG_SZ /d no /f | |
| :: | |
| ::####################################################################### | |
| :: Enable and Configure Google Chrome Internet Browser Settings | |
| ::####################################################################### | |
| :: | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AdvancedProtectionAllowed" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AllowCrossOriginAuthPrompt" /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AlwaysOpenPdfExternally" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AmbientAuthenticationInPrivateModesEnabled" /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AudioCaptureAllowed" /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "AudioSandboxEnabled" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "BlockExternalExtensions" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "DnsOverHttpsMode" /t REG_SZ /d on /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "SSLVersionMin" /t REG_SZ /d tls1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "ScreenCaptureAllowed" /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "SitePerProcess" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "TLS13HardeningForLocalAnchorsEnabled" /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Google\Chrome" /v "VideoCaptureAllowed" /t REG_DWORD /d 0 /f | |
| :: | |
| ::####################################################################### | |
| :: Enable and Configure Microsoft Office Security Settings | |
| ::####################################################################### | |
| :: | |
| :: Harden all version of MS Office itself against common malspam attacks | |
| :: Disables Macros, enables ProtectedView | |
| :: --------------------- | |
| reg add "HKCU\Software\Policies\Microsoft\Office\12.0\Publisher\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\12.0\Word\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\14.0\Publisher\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\14.0\Word\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\Outlook\Security" /v markinternalasunsafe /t REG_DWORD /d 0 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\Word\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\Excel\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\PowerPoint\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\Word\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\15.0\Publisher\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\Outlook\Security" /v markinternalasunsafe /t REG_DWORD /d 0 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\Word\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\Excel\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\PowerPoint\Security" /v blockcontentexecutionfrominternet /t REG_DWORD /d 1 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\Word\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| reg add "HKCU\Software\Policies\Microsoft\Office\16.0\Publisher\Security" /v vbawarnings /t REG_DWORD /d 4 /f | |
| :: | |
| :: Harden all version of MS Office itself against DDE malspam attacks | |
| :: Disables Macros, enables ProtectedView | |
| :: --------------------- | |
| :: | |
| reg add "HKCU\Software\Microsoft\Office\14.0\Word\Options" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| reg add "HKCU\Software\Microsoft\Office\14.0\Word\Options\WordMail" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| reg add "HKCU\Software\Microsoft\Office\15.0\Word\Options" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| reg add "HKCU\Software\Microsoft\Office\15.0\Word\Options\WordMail" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| reg add "HKCU\Software\Microsoft\Office\16.0\Word\Options" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| reg add "HKCU\Software\Microsoft\Office\16.0\Word\Options\WordMail" /v DontUpdateLinks /t REG_DWORD /d 00000001 /f | |
| :: | |
| ::####################################################################### | |
| :: Enable and Configure General Windows Security Settings | |
| ::####################################################################### | |
| :: Disables DNS multicast, smart mutli-homed resolution, netbios, powershellv2, printer driver download and printing over http, icmp redirect | |
| :: Enables UAC and sets to always notify, Safe DLL loading (DLL Hijacking prevention), saving zone information, explorer DEP, explorer shell protocol protected mode | |
| :: --------------------- | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" /v EnableMulticast /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" /v DisableSmartNameResolution /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters" /v DisableParallelAandAAAA /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" /v SMB1 /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v IGMPLevel /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v DisableIPSourceRouting /t REG_DWORD /d 2 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v EnableICMPRedirect /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters" /v DisableIPSourceRouting /t REG_DWORD /d 2 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v EnableLUA /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v EnableVirtualization /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 2 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager" /v SafeDLLSearchMode /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager" /v ProtectionMode /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Attachments" /v SaveZoneInformation /t REG_DWORD /d 2 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Explorer" /v NoDataExecutionPrevention /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Explorer" /v NoHeapTerminationOnCorruption /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v PreXPSP2ShellProtocolBehavior /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers" /v DisableWebPnPDownload /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers" /v DisableHTTPPrinting /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\WcmSvc\wifinetworkmanager\config" /v AutoConnectAllowedOEM /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WcmSvc\GroupPolicy" /v fMinimizeConnections /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Netbt\Parameters" /v NoNameReleaseOnDemand /t REG_DWORD /d 1 /f | |
| wmic /interactive:off nicconfig where (TcpipNetbiosOptions=0 OR TcpipNetbiosOptions=1) call SetTcpipNetbios 2 | |
| powershell.exe Disable-WindowsOptionalFeature -Online -FeatureName MicrosoftWindowsPowerShellV2 -norestart | |
| powershell.exe Disable-WindowsOptionalFeature -Online -FeatureName MicrosoftWindowsPowerShellV2Root -norestart | |
| :: | |
| :: Prioritize ECC Curves with longer keys | |
| ::reg add "HKLM\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\00010002" /v EccCurves /t REG_MULTI_SZ /d NistP384,NistP256 /f | |
| :: Prevent Kerberos from using DES or RC4 | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters" /v SupportedEncryptionTypes /t REG_DWORD /d 2147483640 /f | |
| :: Encrypt and sign outgoing secure channel traffic when possible | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" /v SealSecureChannel /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" /v SignSecureChannel /t REG_DWORD /d 1 /f | |
| :: | |
| :: Enable SmartScreen | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\System" /v EnableSmartScreen /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\System" /v ShellSmartScreenLevel /t REG_SZ /d Block /f | |
| :: | |
| :: Enforce device driver signing | |
| BCDEDIT /set nointegritychecks OFF | |
| :: | |
| :: Windows Update Settings | |
| :: Prevent Delivery Optimization from downloading Updates from other computers across the internet | |
| :: 1 will restrict to LAN only. 0 will disable the feature entirely | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DeliveryOptimization" /v DODownloadMode /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config\" /v DODownloadMode /t REG_DWORD /d 1 /f | |
| :: | |
| :: Set screen saver inactivity timeout to 15 minutes | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v InactivityTimeoutSecs /t REG_DWORD /d 900 /f | |
| :: Enable password prompt on sleep resume while plugged in and on battery | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Power\PowerSettings\0e796bdb-100d-47d6-a2d5-f7d2daa51f51" /v ACSettingIndex /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Power\PowerSettings\0e796bdb-100d-47d6-a2d5-f7d2daa51f51" /v DCSettingIndex /t REG_DWORD /d 1 /f | |
| :: | |
| :: Windows Remote Access Settings | |
| :: Disable solicited remote assistance | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fAllowToGetHelp /t REG_DWORD /d 0 /f | |
| :: Require encrypted RPC connections to Remote Desktop | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fEncryptRPCTraffic /t REG_DWORD /d 1 /f | |
| :: Prevent sharing of local drives via Remote Desktop Session Hosts | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fDisableCdm /t REG_DWORD /d 1 /f | |
| :: | |
| :: Removal Media Settings | |
| :: Disable autorun/autoplay on all drives | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Explorer" /v NoAutoplayfornonVolume /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer" /v NoDriveTypeAutoRun /t REG_DWORD /d 255 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v NoAutorun /t REG_DWORD /d 1 /f | |
| :: | |
| :: Windows Sharing/SMB Settings | |
| :: Disable smb1, anonymous access to named pipes/shared, anonymous enumeration of SAM accounts, non-admin remote access to SAM | |
| :: Enable optional SMB client signing | |
| powershell.exe Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol -norestart | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\mrxsmb10" /v Start /t REG_DWORD /d 4 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" /v SMB1 /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters" /v RestrictNullSessAccess /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictAnonymousSAM /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictAnonymous /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v EveryoneIncludesAnonymous /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictRemoteSAM /t REG_SZ /d "O:BAG:BAD:(A;;RC;;;BA)" /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v UseMachineId /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v LimitBlankPasswordUse /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\LSA\MSV1_0" /v allownullsessionfallback /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters" /v EnableSecuritySignature /t REG_DWORD /d 1 /f | |
| :: Force SMB server signing | |
| :: This could cause impact if the Windows computer this is run on is hosting a file share and the other computers connecting to it do not have SMB client signing enabled. | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters" /v RequireSecuritySignature /t REG_DWORD /d 1 /f | |
| :: | |
| :: Harden lsass to help protect against credential dumping (mimikatz) and audit lsass access requests | |
| :: Configures lsass.exe as a protected process and disables wdigest | |
| :: Enables delegation of non-exported credentials which enables support for Restricted Admin Mode or Remote Credential Guard | |
| :: --------------------- | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LSASS.exe" /v AuditLevel /t REG_DWORD /d 00000008 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPL /t REG_DWORD /d 00000001 /f | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest" /v UseLogonCredential /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation" /v AllowProtectedCreds /t REG_DWORD /d 1 /f | |
| :: | |
| :: Windows RPC and WinRM settings | |
| :: Stop WinRM | |
| net stop WinRM | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WinRM\Service" /v AllowUnencryptedTraffic /t REG_DWORD /d 0 /f | |
| :: Disable WinRM Client Digiest authentication | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WinRM\Client" /v AllowDigest /t REG_DWORD /d 0 /f | |
| :: Disabling RPC usage from a remote asset interacting with scheduled tasks | |
| reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule" /v DisableRpcOverTcp /t REG_DWORD /d 1 /f | |
| :: Disabling RPC usage from a remote asset interacting with services | |
| reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control" /v DisableRemoteScmEndpoints /t REG_DWORD /d 1 /f | |
| :: | |
| :: Biometrics | |
| :: Enable anti-spoofing for facial recognition | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Biometrics\FacialFeatures" /v EnhancedAntiSpoofing /t REG_DWORD /d 1 /f | |
| :: Disable other camera use while screen is locked | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Personalization" /v NoLockScreenCamera /t REG_DWORD /d 1 /f | |
| :: Prevent Windows app voice activation while locked | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\AppPrivacy" /v LetAppsActivateWithVoiceAboveLock /t REG_DWORD /d 2 /f | |
| :: Prevent Windows app voice activation entirely (be mindful of those with accesibility needs) | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\AppPrivacy" /v LetAppsActivateWithVoice /t REG_DWORD /d 2 /f | |
| :: | |
| ::####################################################################### | |
| :: Enable and configure Windows Firewall | |
| ::####################################################################### | |
| :: | |
| NetSh Advfirewall set allprofiles state on | |
| :: | |
| :: Enable Firewall Logging | |
| netsh advfirewall set currentprofile logging filename %systemroot%\system32\LogFiles\Firewall\pfirewall.log | |
| netsh advfirewall set currentprofile logging maxfilesize 4096 | |
| netsh advfirewall set currentprofile logging droppedconnections enable | |
| :: | |
| :: Block all inbound connections on Public profile | |
| netsh advfirewall set publicprofile firewallpolicy blockinboundalways,allowoutbound | |
| :: Enable Windows Defender Network Protection | |
| powershell.exe Set-MpPreference -EnableNetworkProtection Enabled | |
| :: | |
| :: Block Win32 binaries from making netconns when they shouldn't - specifically targeting native processes known to be abused by bad actors | |
| :: --------------------- | |
| Netsh.exe advfirewall firewall add rule name="Block Notepad.exe netconns" program="%systemroot%\system32\notepad.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block regsvr32.exe netconns" program="%systemroot%\system32\regsvr32.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block calc.exe netconns" program="%systemroot%\system32\calc.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block mshta.exe netconns" program="%systemroot%\system32\mshta.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block wscript.exe netconns" program="%systemroot%\system32\wscript.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block cscript.exe netconns" program="%systemroot%\system32\cscript.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block runscripthelper.exe netconns" program="%systemroot%\system32\runscripthelper.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| Netsh.exe advfirewall firewall add rule name="Block hh.exe netconns" program="%systemroot%\system32\hh.exe" protocol=tcp dir=out enable=yes action=block profile=any | |
| :: | |
| ::Netsh.exe int ipv6 set int *INTERFACENUMBER* rabaseddnsconfig=disable | |
| ::https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-16898 | |
| ::####################################################################### | |
| :: Windows 10 Privacy Settings | |
| ::####################################################################### | |
| :: | |
| :: Set Windows Analytics to limited enhanced if enhanced is enabled | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v LimitEnhancedDiagnosticDataWindowsAnalytics /t REG_DWORD /d 1 /f | |
| :: Set Windows Telemetry to security only | |
| :: If you intend to use Enhanced for Windows Analytics then set this to "2" instead | |
| :: Note my understanding is W10 Home edition will do a minimum of "Basic" | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v AllowTelemetry /t REG_DWORD /d 0 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v MaxTelemetryAllowed /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Diagnostics\DiagTrack" /v ShowedToastAtLevel /t REG_DWORD /d 1 /f | |
| :: Disable location data | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\CapabilityAccessManager\ConsentStore" /v Location /t REG_SZ /d Deny /f | |
| :: Prevent the Start Menu Search from providing internet results and using your location | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Search" /v BingSearchEnabled /t REG_DWORD /d 0 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Search" /v AllowSearchToUseLocation /t REG_DWORD /d 0 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Search" /v CortanaConsent /t REG_DWORD /d 0 /f | |
| :: Disable publishing of Win10 user activity | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\System" /v PublishUserActivities /t REG_DWORD /d 1 /f | |
| :: Disable Win10 settings sync to cloud | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\SettingSync" /v DisableSettingSync /t REG_DWORD /d 2 /f | |
| :: Disable the advertising ID | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\AdvertisingInfo" /v DisabledByGroupPolicy /t REG_DWORD /d 1 /f | |
| :: | |
| :: Disable Windows GameDVR (Broadcasting and Recording) | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\GameDVR" /v AllowGameDVR /t REG_DWORD /d 0 /f | |
| :: Disable Microsoft consumer experience which prevent notifications of suggested applications to install | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\CloudContent" /v DisableWindowsConsumerFeatures /t REG_DWORD /d 1 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager" /v SystemPaneSuggestionsEnabled /t REG_DWORD /d 0 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager" /v SilentInstalledAppsEnabled /t REG_DWORD /d 0 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager" /v PreInstalledAppsEnabled /t REG_DWORD /d 0 /f | |
| reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager" /v OemPreInstalledAppsEnabled /t REG_DWORD /d 0 /f | |
| :: Disable websites accessing local language list | |
| reg add "HKCU\Control Panel\International\User Profile" /v HttpAcceptLanguageOptOut /t REG_DWORD /d 1 /f | |
| :: Prevent toast notifications from appearing on lock screen | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\PushNotifications" /v NoToastApplicationNotificationOnLockScreen /t REG_DWORD /d 1 /f | |
| :: | |
| ::####################################################################### | |
| :: Enable Advanced Windows Logging | |
| ::####################################################################### | |
| :: | |
| :: Enlarge Windows Event Security Log Size | |
| wevtutil sl Security /ms:1024000 | |
| wevtutil sl Application /ms:1024000 | |
| wevtutil sl System /ms:1024000 | |
| wevtutil sl "Windows Powershell" /ms:1024000 | |
| wevtutil sl "Microsoft-Windows-PowerShell/Operational" /ms:1024000 | |
| :: Record command line data in process creation events eventid 4688 | |
| reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Audit" /v ProcessCreationIncludeCmdLine_Enabled /t REG_DWORD /d 1 /f | |
| :: | |
| :: Enabled Advanced Settings | |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v SCENoApplyLegacyAuditPolicy /t REG_DWORD /d 1 /f | |
| :: Enable PowerShell Logging | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell\ModuleLogging" /v EnableModuleLogging /t REG_DWORD /d 1 /f | |
| reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging" /v EnableScriptBlockLogging /t REG_DWORD /d 1 /f | |
| :: | |
| :: Enable Windows Event Detailed Logging | |
| :: This is intentionally meant to be a subset of expected enterprise logging as this script may be used on consumer devices. | |
| :: For more extensive Windows logging, I recommend https://www.malwarearchaeology.com/cheat-sheets | |
| Auditpol /set /subcategory:"Security Group Management" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"Process Creation" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"Logoff" /success:enable /failure:disable | |
| Auditpol /set /subcategory:"Logon" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"Filtering Platform Connection" /success:enable /failure:disable | |
| Auditpol /set /subcategory:"Removable Storage" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"SAM" /success:disable /failure:disable | |
| Auditpol /set /subcategory:"Filtering Platform Policy Change" /success:disable /failure:disable | |
| Auditpol /set /subcategory:"IPsec Driver" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"Security State Change" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"Security System Extension" /success:enable /failure:enable | |
| Auditpol /set /subcategory:"System Integrity" /success:enable /failure:enable | |
| :: | |
| ::####################################################################### | |
| :: Extra settings commented out but worth considering | |
| ::####################################################################### | |
| :: | |
| :: Uninstall common extra apps found on a lot of Win10 installs | |
| :: Obviously do a quick review to ensure it isn't removing any apps you or your user need to use. | |
| :: https://docs.microsoft.com/en-us/windows/application-management/apps-in-windows-10 | |
| :: PowerShell command to reinstall all pre-installed apps below | |
| :: Get-AppxPackage -AllUsers| Foreach {Add-AppxPackage -DisableDevelopmentMode -Register "$($_.InstallLocation)\AppXManifest.xml"} | |
| powershell.exe -command "Get-AppxPackage *Microsoft.BingWeather* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.DesktopAppInstaller* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.GetHelp* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Getstarted* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Messaging* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.OneConnect* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Print3D* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.SkypeApp* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Wallet* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.WindowsAlarms* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.WindowsCamera* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *microsoft.windowscommunicationsapps* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.WindowsFeedbackHub* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.WindowsSoundRecorder* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.YourPhone* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.WindowsFeedback* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Windows.ContactSupport* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *PandoraMedia* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *AdobeSystemIncorporated. AdobePhotoshop* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Duolingo* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.BingNews* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Office.Sway* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *Microsoft.Advertising.Xaml* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *ActiproSoftware* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *EclipseManager* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *SpotifyAB.SpotifyMusic* -AllUsers | Remove-AppxPackage" | |
| powershell.exe -command "Get-AppxPackage *king.com.* -AllUsers | Remove-AppxPackage" | |
| :: Removed Provisioned Apps | |
| :: This will prevent these apps from being reinstalled on new user first logon | |
| :: Obviously I manually chose this list. If you truly want to nuke all the provisioned apps, you can use the below commented command in PowerShell | |
| :: Get-AppXProvisionedPackage -Online | Remove-AppxProvisionedPackage -Online | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.BingWeather'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.GetHelp'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.Getstarted'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.SkypeApp'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.WindowsAlarms'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.WindowsCamera'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'microsoft.windowscommunicationsapps'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.WindowsFeedbackHub'} | Remove-AppxProvisionedPackage -Online" | |
| powershell.exe -command "Get-AppxProvisionedPackage -Online | Where-Object {$_.DisplayName -eq 'Microsoft.YourPhone'} | Remove-AppxProvisionedPackage -Online" | |
| :: | |
| ::####################################################################### | |
| :: Extra settings commented out but worth considering | |
| ::####################################################################### | |
| :: | |
| :: Enforce NTLMv2 and LM authentication | |
| :: This is commented out by default as it could impact access to consumer-grade file shares but it's a recommended setting | |
| :: reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v LmCompatibilityLevel /t REG_DWORD /d 5 /f | |
| :: | |
| :: Prevent unencrypted passwords being sent to third-party SMB servers | |
| :: This is commented out by default as it could impact access to consumer-grade file shares but it's a recommended setting | |
| :: reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters" /v EnablePlainTextPassword /t REG_DWORD /d 0 /f | |
| :: | |
| :: Prevent guest logons to SMB servers | |
| :: This is commented out by default as it could impact access to consumer-grade file shares but it's a recommended setting | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\LanmanWorkstation" /v AllowInsecureGuestAuth /t REG_DWORD /d 0 /f | |
| :: | |
| :: Force SMB server signing | |
| :: This is commented out by default as it could impact access to consumer-grade file shares but it's a recommended setting | |
| :: reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters" /v RequireSecuritySignature /t REG_DWORD /d 1 /f | |
| :: | |
| :: Enable Windows Defender Application Guard | |
| :: This setting is commented out as it enables subset of DC/CG which renders other virtualization products unsuable. Can be enabled if you don't use those | |
| :: powershell.exe Enable-WindowsOptionalFeature -online -FeatureName Windows-Defender-ApplicationGuard -norestart | |
| :: | |
| :: Enable Windows Defender Credential Guard | |
| :: This setting is commented out as it enables subset of DC/CG which renders other virtualization products unsuable. Can be enabled if you don't use those | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard" /v EnableVirtualizationBasedSecurity /t REG_DWORD /d 1 /f | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard" /v RequirePlatformSecurityFeatures /t REG_DWORD /d 3 /f | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard" /v LsaCfgFlags /t REG_DWORD /d 1 /f | |
| :: | |
| :: The following variant also enables forced ASLR and CFG but causes issues with several third party apps | |
| :: powershell.exe Set-Processmitigation -System -Enable DEP,CFG,ForceRelocateImages,BottomUp,SEHOP | |
| :: | |
| :: Block executable files from running unless they meet a prevalence, age, or trusted list criterion | |
| :: This one is commented out for now as I need to research and test more to determine potential impact | |
| :: powershell.exe Add-MpPreference -AttackSurfaceReductionRules_Ids 01443614-cd74-433a-b99e-2ecdc07bfc25 -AttackSurfaceReductionRules_Actions Enabled | |
| :: | |
| :: Enable Windows Defender real time monitoring | |
| :: Commented out given consumers often run third party anti-virus. You can run either. | |
| :: powershell.exe -command "Set-MpPreference -DisableRealtimeMonitoring $false" | |
| :: reg add "HKLM\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 0 /f | |
| :: | |
| :: Disable internet connection sharing | |
| :: Commented out as it's not enabled by default and if it is enabled, may be for a reason | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Network Connections" /v NC_ShowSharedAccessUI /t REG_DWORD /d 0 /f | |
| :: | |
| :: Always re-process Group Policy even if no changes | |
| :: Commented out as consumers don't typically use GPO | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Group Policy\{35378EAC-683F-11D2-A89A-00C04FBBCFA2}" /v NoGPOListChanges /t REG_DWORD /d 0 /f | |
| :: | |
| :: Force logoff if smart card removed | |
| :: Set to "2" for logoff, set to "1" for lock | |
| :: Commented out as consumers don't typically use smart cards | |
| :: reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v SCRemoveOption /t REG_DWORD /d 2 /f | |
| :: | |
| :: Restrict privileged local admin tokens being used from network | |
| :: Commented out as it only works on domain-joined assets | |
| :: reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 0 /f | |
| :: | |
| :: Ensure outgoing secure channel traffic is encrytped | |
| :: Commented out as it only works on domain-joined assets | |
| :: reg add "HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" /v RequireSignOrSeal /t REG_DWORD /d 1 /f | |
| :: | |
| :: Enforce LDAP client signing | |
| :: Commented out as most consumers don't use LDAP auth | |
| :: reg add "HKLM\SYSTEM\CurrentControlSet\Services\LDAP" /v LDAPClientIntegrity /t REG_DWORD /d 1 /f | |
| :: | |
| :: Prevent unauthenticated RPC connections | |
| :: reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Rpc" /v RestrictRemoteClients /t REG_DWORD /d 1 /f | |
| :: | |
| ::####################################################################### | |
| :: References | |
| ::####################################################################### | |
| :: | |
| :: LLMNR | |
| :: https://www.blackhillsinfosec.com/how-to-disable-llmnr-why-you-want-to/ | |
| :: | |
| :: Windows Defender References | |
| :: ASR Rules https://www.darkoperator.com/blog/2017/11/11/windows-defender-exploit-guard-asr-rules-for-office | |
| :: ASR and Exploit Guard https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-exploit-guard/attack-surface-reduction-exploit-guard | |
| :: ASR Rules https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/attack-surface-reduction | |
| :: Easy methods to test rules https://demo.wd.microsoft.com/?ocid=cx-wddocs-testground | |
| :: Resource on the rules and associated event IDs https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/event-views | |
| :: Defender sandboxing https://cloudblogs.microsoft.com/microsoftsecure/2018/10/26/windows-defender-antivirus-can-now-run-in-a-sandbox/ | |
| :: Defender exploit protection https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-exploit-guard/customize-exploit-protection | |
| :: Application Guard https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-guard/install-wd-app-guard | |
| :: Defender cmdline https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-antivirus/command-line-arguments-windows-defender-antivirus | |
| :: | |
| :: General hardening references | |
| :: LSA Protection https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn408187(v=ws.11)?redirectedfrom=MSDN | |
| :: | |
| :: Microsoft Office References: | |
| :: Disable DDE https://gist.github.com/wdormann/732bb88d9b5dd5a66c9f1e1498f31a1b | |
| :: Disable macros https://decentsecurity.com/block-office-macros/ | |
| :: | |
| :: Debloating | |
| :: https://blog.danic.net/how-windows-10-pro-installs-unwanted-apps-candy-crush-and-how-you-stop-it/ | |
| :: Frameworks and benchmarks | |
| :: STIG https://www.stigviewer.com/stig/windows_10/ | |
| pause |
Back to my MS Teams issue. There were multiple issues and I lost patience and track of the changes after a while. Firewall was an issue at first because my home WiFi was set to a public profile, not private. Exploitguard didn't fix it. I think that it was related to transport layer and credential security issues (encryption methods, signing, secure channel, LmCompatibilityLevel, UseLogonCredential, AllowProtectedCreds, etc.)
Some really good stuff in this, thank you!
Thank you very much for putting time and effort into compiling and testing ⭐. This script and your references was one of the big inspiration when I built privacy.sexy (a GUI around the scripts) 🍻
The following line causes Windows Update to fail as well as other MS remote things (i.e. powerpoint template loading)
reg add "HKLM\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\00010002" /v EccCurves /t REG_MULTI_SZ /d NistP384,NistP256 /f
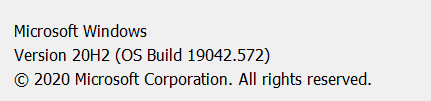
Windows 10 1909 (OS Build 18363.1082)
Removing the EccCurves key and a reboot fixes the issue.
I ran into the same issue as @kernel-sanders, this key made many of my programs stop working, including docker, krisp, chocolatey, windows update, and many more.
All the errors in event viewer registered similar logs in event viewer:
Faulting application name: choco.exe, version: 0.10.5.0, time stamp: 0x58e7c338
Faulting module name: ntdll.dll, version: 10.0.19041.546, time stamp: 0x5b56177b
Exception code: 0xc0000409
Fault offset: 0x00000000000a1090
Faulting process ID: 0x1ef4
Faulting application start time: 0x01d6a233efda9233
Faulting application path: C:\ProgramData\chocolatey\bin\choco.exe
Faulting module path: C:\Windows\SYSTEM32\ntdll.dll
Report ID: 24171f6f-1e0b-4a34-a103-ff9404943489
Faulting package full name:
Faulting package-relative application ID:
Thank you for the feedback! I will comment it out for now.
Thanks for putting this together! This is great. I can confirm what @kernel-sanders and @evilpilaf are saying, that EccCurves breaks a lot of apps.
After I ran this script, a lot of our users including myself can't print to our home Wi-Fi printers anymore. Any guess what would be break that? I'm having a hard time figuring out. It seems like most home Wi-Fi printers are setup to print via IPP (internet printing protocol). I've tried deleted all the registry changes and rebooting, but I still can't seem to re-install a home Wi-Fi printer and print.
@TwKROazGKsh it is possibly the two following rules:
reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v IGMPLevel /t REG_DWORD /d 0 /f
netsh advfirewall set publicprofile firewallpolicy blockinboundalways,allowoutbound
Revert them with
reg delete "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v IGMPLevel /f
netsh advfirewall reset
Thanks @kernel-sanders, that help! It turns out you had to add the default value back for IGMPLevel=2, so printing via multicast works. Just deleting the registry key and rebooting did not fix it.
reg add "HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters" /v IGMPLevel /t REG_DWORD /d 2 /f
After you add that back, you'll need to reboot for it to take affect. It seems like the default Windows 10 printer setup GUI, configures the printer using WSD (Web Services for Devices), which uses ipv4 multicast.
FYI - we did not push that firewall rule to our users, so we did not have to revert that one, but my guess is it will likely cause other issues too if your users don't have their Wi-Fi/ethernet connection set to private/domain profile.
Very nice script Mackwage.
Any chance you can add a couple lines for the Windows Shadow Copy vulnerabilities? CVE-2021-36934
I believe it uses a combination of icalcs and vssadmin commands to set permissions and delete previous shadow copies that are vulnerable.
https://labs.k7computing.com/?vulnerability=cve-2021-36934
Much obliged and great work here.
Why block notepad and calc? Also, why not by default block nbns and llmnr?
Thank you for the effort that went into this. A great resource. I'm hoping that it will solve my problems with pesky nuisance hackers.
Excellent script - thank you.
As far as changing file associations to Notepad.exe, the method at the top of this script is for cmd only and not Powershell. After some brief testing, the equivalent PowerShell format is:
#Change double-click of .bat files to open in Notepad
CMD: ftype batfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1"
PowerShell: cmd /c --% ftype batfile="%SystemRoot%\system32\NOTEPAD.EXE" "%1"
This is really great. It would be even greater if there was a script to reverse all the changes in case some cause issues. (or add the comands as commetns.)
The whole script is super cool!! Do you have the script to reverse all the changes?
This is really great. It would be even greater if there was a script to reverse all the changes in case some cause issues. (or add the comands as commetns.)
I second this!
@RobertLaffan Just curious if you worked on reverse script?
Executing reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config" results in a Config" subkey being created under ..."DeliveryOptimization". The subkey contains the double quote. Win11 Pro 21H2.
Anyone else having the same issue?
Indeed, yeah I think that's a typo. It can be simply fixed by just adding another backslash to the end of the path, before the quotation mark. So, amend that line to reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DeliveryOptimization\Config\" /v DODownloadMode /t REG_DWORD /d 1 /f
And then, of course, feel free to clean up/delete that Config" registry.
amazing your disabling of windows file explorer on new volumes, media and partitions works! I was able to fix my installer script when partitioning hard drives without format pop up spams and explorer popups galore. Your even better then chat gpt
Do the office hardening settings block plugins like copilot? Specifically the attack surface reduction and the prevention of spawning child processes.
Found a couple issues so far
change all microsoft office settings from hard coded say 14.0 to a for loop of all versions
since you added calc also add icacls to the firewall
Most probably the correct command for changing the EccCurves registry key is:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Cryptography\Configuration\SSL\00010002" /v EccCurves /t REG_MULTI_SZ /d "NistP384"\0"NistP256" /f
as it is a REG_MULTI_SZ and expects the strings separated by the zero byte. That may be why it caused problems.
Great attention to detail. That seems to properly format the key to have the appropriate two values, instead of it being misformatted as one.
Thanks!

Yeah. You have to explicitly set an open firewall rule. You could tie it to the TightVNC binary or the port number itself (or both). When I'm back at my computer, I can look up the command(s)