-
-
Save misostack/31c5599b7f589d6cbea4f6fae5ce7eb2 to your computer and use it in GitHub Desktop.
How to create a secure AWS RDS instances in private subnet
You can't select subnet for your AWS DB Instances
Managed-RDS: MYSQL, PostgreSQL ( Full Managed )
RDS Aurora (Full Managed and ServerLess)
All you need to do is
- Create subnets in diffrent AZs
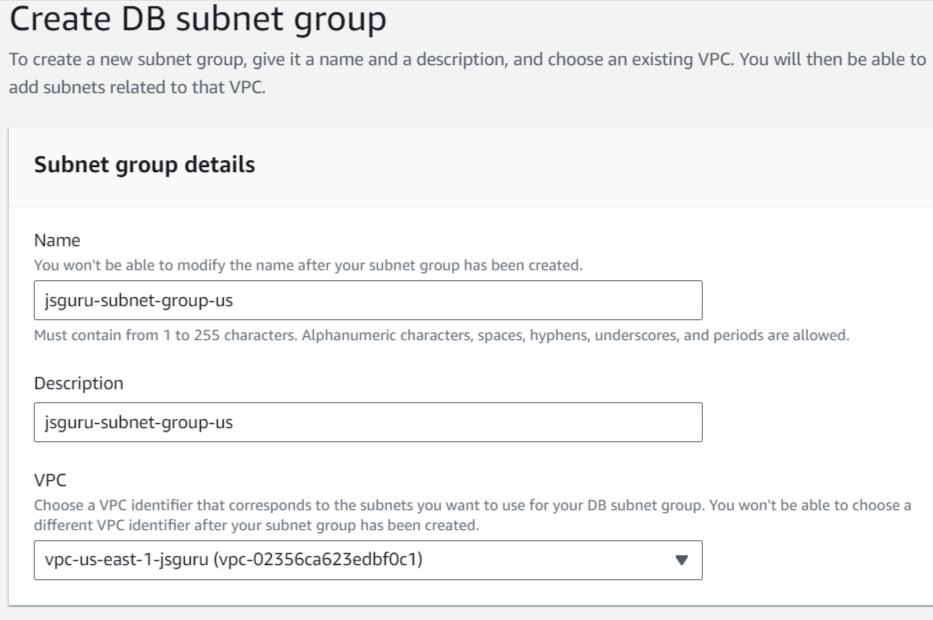
- Create subnet group
- Select VPC
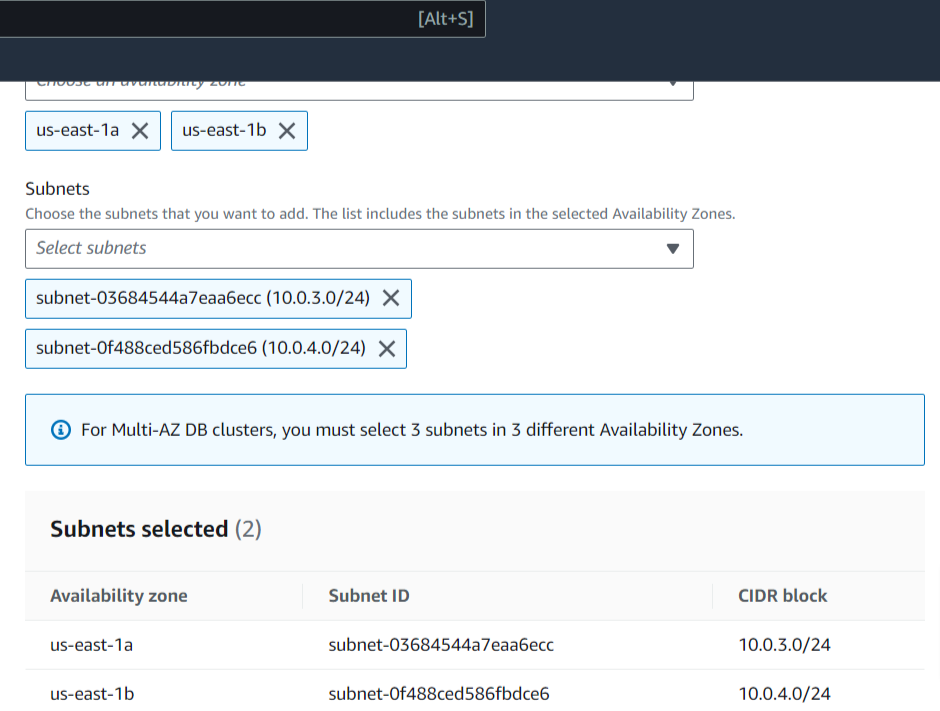
- Select AZs
- Select Subnets
Create subnets in diffrent AZs
Create subnet group and select your VPC, AZs, Subnets
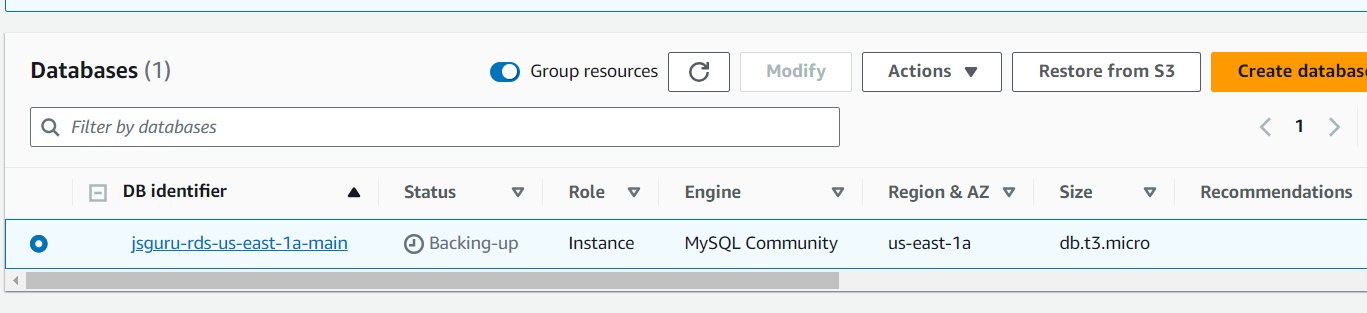
Create your RDS instance with selected VPC, subnet group, AZ
Grab a cup of coffee while you're waiting for your RDS instance is ready to used
Test connection with nodejs and mysql2 package
const mysql = require("mysql2");
var connection = mysql.createConnection({
host: "jsguru-rds-us-east-1a-main.c5u2qmocqh5e.us-east-1.rds.amazonaws.com",
user: "jsguru",
password: "12345678",
port: 3306,
});
connection.connect(function (err) {
if (err) {
console.error("Database connection failed: " + err.stack);
return;
}
console.log("Connected to database.");
});
connection.end();RDS Proxy
Any DB instance that encounters "too many connections" errors is a good candidate for associating with a proxy. This is often characterized by a high value of the ConnectionAttempts CloudWatch metric. The proxy enables applications to open many client connections, while the proxy manages a smaller number of long-lived connections to the DB instance
Monitor with CloudWatch
Install CloudWatchAgent
Create an IAM Role
Install CloudWatch
wget https://amazoncloudwatch-agent.s3.amazonaws.com/ubuntu/amd64/latest/amazon-cloudwatch-agent.deb
sudo dpkg -i -E ./amazon-cloudwatch-agent.debAttach IAM Role
Install aws cli and test
sudo apt install unzip
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/installCreate config file
sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-config-wizardStart
sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl -a fetch-config -m ec2 -s -c file:/opt/aws/amazon-cloudwatch-agent/bin/config.jsonSample config
{
"agent": {
"metrics_collection_interval": 60,
"run_as_user": "cwagent"
},
"metrics": {
"aggregation_dimensions": [["InstanceId"]],
"append_dimensions": {
"AutoScalingGroupName": "${aws:AutoScalingGroupName}",
"ImageId": "${aws:ImageId}",
"InstanceId": "${aws:InstanceId}",
"InstanceType": "${aws:InstanceType}"
},
"metrics_collected": {
"cpu": {
"measurement": [
"cpu_usage_idle",
"cpu_usage_iowait",
"cpu_usage_user",
"cpu_usage_system"
],
"metrics_collection_interval": 60,
"resources": ["*"],
"totalcpu": false
},
"disk": {
"measurement": ["used_percent", "inodes_free"],
"metrics_collection_interval": 60,
"resources": ["*"]
},
"diskio": {
"measurement": ["io_time"],
"metrics_collection_interval": 60,
"resources": ["*"]
},
"mem": {
"measurement": ["mem_used_percent"],
"metrics_collection_interval": 60
},
"statsd": {
"metrics_aggregation_interval": 60,
"metrics_collection_interval": 10,
"service_address": ":8125"
},
"swap": {
"measurement": ["swap_used_percent"],
"metrics_collection_interval": 60
}
}
}
}Stress Test
sudo apt install stress
sudo apt install stress-ng
stress-ng --cpu 4 --io 2 --vm 1 --vm-bytes 250m --timeout 60s --metrics-briefCloudWatch Labs
Command to access AWS CLI
sudo apt update -y
sudo apt install unzip -y
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/installCommand to do stress test
sudo apt update -y
sudo apt install stress-ng -y
stress-ng --cpu 4 --io 2 --vm 1 --vm-bytes 250m --timeout 60s --metrics-briefCloudWatch Metrics
CloudWatch Standard Metrics
CloudWatch Custom Metrics
Create Policy, Create Role, and Attach IAM Role for EC2 Instance





Test
aws cloudwatch list-metricsTest put-metric
[
{
"MetricName": "New Posts",
"Timestamp": "Tuesday, January 08, 2024 8:28:20 AM",
"Value": 0.50,
"Unit": "Count"
}
]aws cloudwatch put-metric-data --namespace "JSGuruCustomMetric" --metric-data file://metric.js
aws cloudwatch put-metric-data --metric-name CloudWatchAlarmValue --namespace JSGuruCustomMetric --unit Percent--value 50 --dimensions InstanceID=$(curl -s -X GET -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id),InstanceType=$(curl -s -X GET -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-type)Request EC2 API Token
TOKEN=`curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600"`
echo $TOKENGet EC2 meta-data and user-data
curl -X GET -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data
curl -X GET -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id
curl -X GET -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/user-dataCreate Alarm
Notification
Trigger Lambda Function
Trigger AutoScale Group with Action









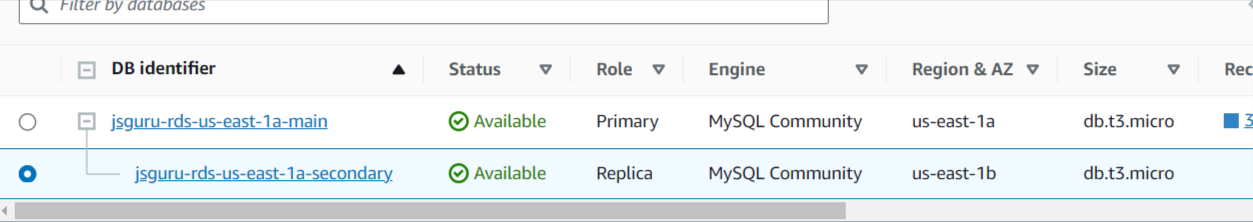






























Open Access from internet
Create InternetGateway and Attach to your VPC
Add new record to your route table that redirect all request from the attached internet gateway to your VPC network

