when HTTP_REQUEST {
# Define the list of domains to block
set blocked_domains { "your-domain01" "your-domain02" }
# Get the Host header value
set host_header [HTTP::host]
# Define the list of dynamic page extensions to block
set dynamic_extensions { ".php" ".asp" ".jsp" ".cgi" ".pl" ".aspx" ".ashx" ".cfm" }
# Loop through the blocked domains and check if the host header matches any
foreach domain $blocked_domains {
if { $host_header equals $domain } {
# Loop through the dynamic page extensions to check if the URI ends with any of them
foreach ext $dynamic_extensions {
if { [string tolower [HTTP::uri]] ends_with $ext } {
# Log the event (optional)
log local0. "Blocking dynamic file request ($ext) to $host_header: [HTTP::uri]"
# Send a custom 403 Forbidden response with HTML content
HTTP::respond 403 content {
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>403 Forbidden</title>
<style>
body {
background-color: #f9f9f9;
font-family: Arial, sans-serif;
text-align: center;
padding: 50px;
}
h1 {
font-size: 100px;
margin: 0;
color: #333;
}
p {
font-size: 24px;
color: #666;
}
</style>
</head>
<body>
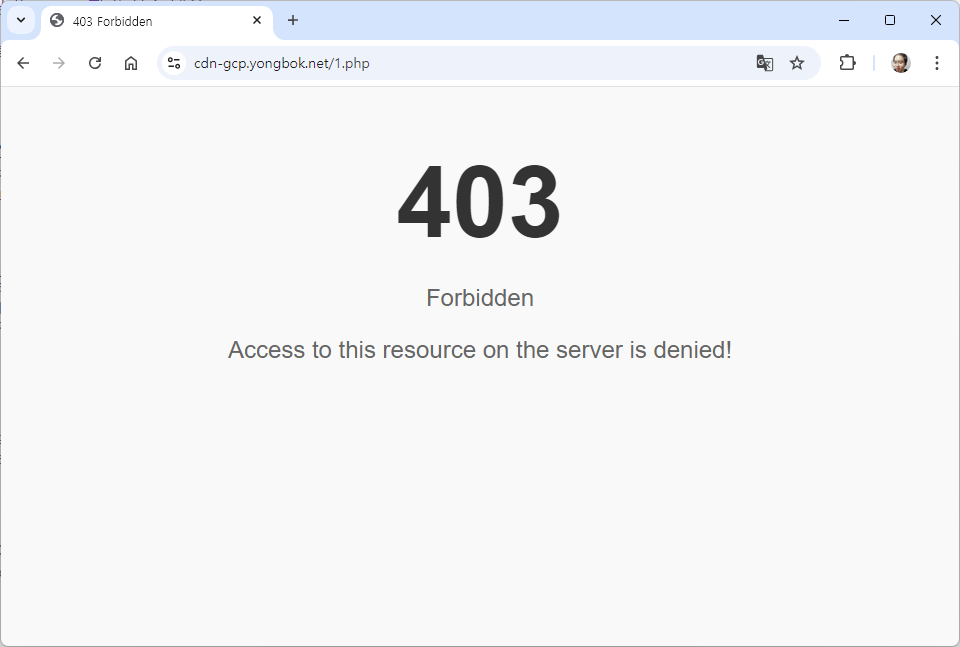
<h1>403</h1>
<p>Forbidden</p>
<p>Access to this resource on the server is denied!</p>
</body>
</html>
} "Content-Type" "text/html"
return
}
}
}
}
}
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: =============================================
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Client xxx.xxx.xxx.xxx:62070 -> cdn-gcp.yongbok.net/1.php (request)
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Host: cdn-gcp.yongbok.net
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Connection: keep-alive
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Cache-Control: max-age=0
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: sec-ch-ua: "Google Chrome";v="129", "Not=A?Brand";v="8", "Chromium";v="129"
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: sec-ch-ua-mobile: ?0
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: sec-ch-ua-platform: "Windows"
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Upgrade-Insecure-Requests: 1
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Sec-Fetch-Site: none
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Sec-Fetch-Mode: navigate
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Sec-Fetch-User: ?1
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Sec-Fetch-Dest: document
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Accept-Encoding: gzip, deflate, br, zstd
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Accept-Language: ko,en-US;q=0.9,en;q=0.8,zh-CN;q=0.7,zh;q=0.6
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: Cookie: TS01bfd0b6=01588602e59f894511ab10ebe10385774ec368efff281ab5e4675c5b3a22310347a79c0d37d3934833f3103a4cd11811cc19e93360; TS01bfd0b6028=014c848aa593a6b1ef6b86ac6b6559bad9d2f25c79fcafec6c9a512e3f7a99cbccca9a6c76df4ce854b93c2f70f05490b9bef80ea9
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: X-Forwarded-For: xxx.xxx.xxx.xxx, xxx.xxx.xxx.xxx
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/X-Forwarded-For <HTTP_REQUEST>: =============================================
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/request-csrf-ssrf-cors-deny <HTTP_REQUEST>: X-Forwarded-For has 2 entries: xxx.xxx.xxx.xxx, xxx.xxx.xxx.xxx
Oct 3 20:02:52 f5.yongbok.net info tmm[20498]: Rule /Common/host-header-deny <HTTP_REQUEST>: Blocking PHP file request to cdn-gcp.yongbok.net: /1.php