Subnets
- Public Subnets can send traffic directly to internet
- Public Subnets are associated with a route table which has a route to an internet gateway.
- Private Subnets can send traffic to internet via a NAT gateway.
- The NAT Gateway resides in the public subnet.
Route Table:
- Set rules for outbound traffic from a subnet.
- Each subnet should be associated with a route table.
Security Groups vs Network ACLs
- SG is instance level security.
- Network ACL is subnet level security.
- Network ACLs can be used to provide an additional level of security over and above your SGs.
NAT Gateway:
- Allow outbound communication from VPC but prevent inbound connections to VPC.
- E.g. if you have DB Servers that need to be updated from timet to time.
- NAT Gateways have Elastic IPs associated with them.
- Route table needs to be updated to point all traffic to internet to the NAT Gateway.
- The NAT Gateway resides in the public subnet.
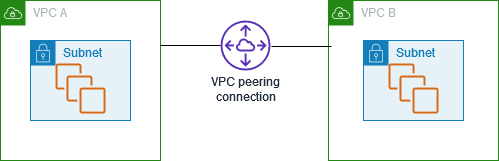
VPC Peering: ref
Allows traffic to flow between 2 VPCs using private IPs.
- Each VPC in the peering request needs to have a different address block.
- VPC peering request needs to be placed and accepted by the "acceptor" VPC before peering is active.
- Route table for each VPC needs to have a route to the other VPC.
Example VPC Peering config:
- VPC A here could contain an Ansible controller as well as other resources such as file shares.
- VPCs B and C could be 2 environments for your application. They do not need to communicate with each other but they do need to be accessible by the Ansible controller in VPC A.
VPC Endpoints: ref
What if an instance within your VPC needs to access an S3 Bucket?
Ans: Create a VPC Endpoint in your VPC to point to the S3 Bucket.