This integration would allow Fastly users to detect and remediate malevolent IPs using CrowdSec. This will be achieved by :
- Leveraging Fastly's ability to forward logs to a Syslog server of the user's choice.
- CrowdSec would consume the logs from the syslog server. It will detect and report malevolent IPs to Fastly bouncer.
- The fastly bouncer would make changes in the Fastly configuration to actualize suggestions made by CrowdSec.
Following proposal contains details about (3)
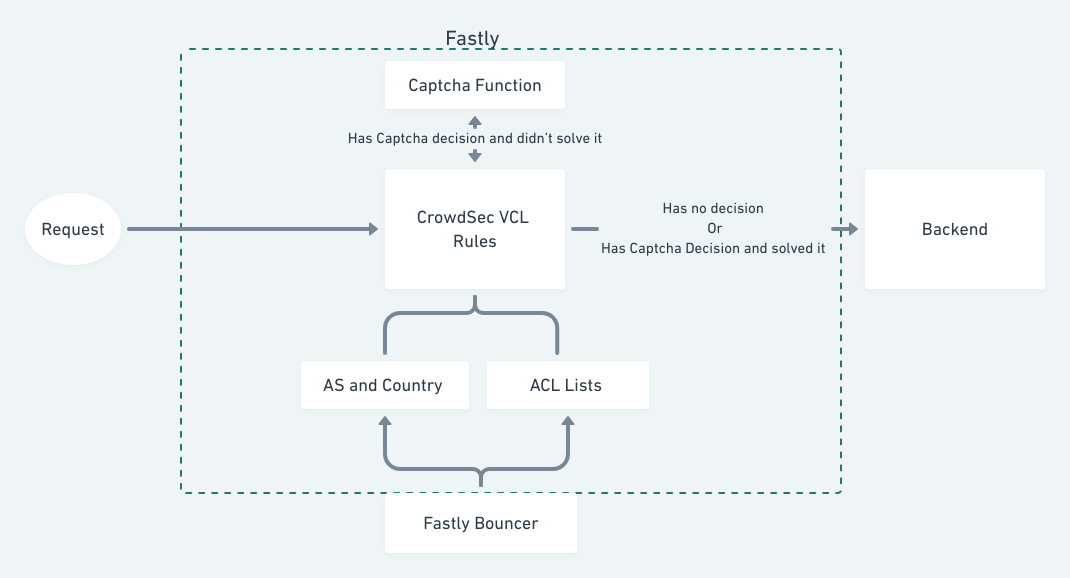
- The bouncer implements captcha and block remediations.
- It can apply these remediations at the level of IP, IP range, AS and Country.
- It deploys the infrastructure required for (2).
- It allows cleaning up the infrastructure it deployed.
Fastly's serverless functions would be used for: Presenting and validating the captcha. This will be provisioned by the bouncer hence no changes to the actual application would be required.
The VCL would contain rules which references some ACLs (Access Control Lists) and determine whether to allow/deny/captcha a request. ACLs are used only for providing IP, IP range scoped remediations.
Country and AS scoped remediations would be taken care by the bouncer by modifying the rules inplace.
After providing the initial setup, the bouncer would do the following:
- Sync CrowdSec's decisions with ACLs.
- Update rules if received AS, country scoped decisions.
- Maintain state of ACLs and the rules.
The bouncer would heavily rely on fastly's terraform provider. This approach has following benefits.
- Free Infra State Management (handled by tf)
- No need to have code to make API calls to Fastly. This means 0 maintenance even if API is changed.
One tricky thing to handle is ACLs. 1 ACL can contain atmost 1k IPs . To get around this multiple ACLs would be created and new IPs would be "loadbalanced" into them.
So effectively we would be writing code which does
- Construct initial terraform config by importing user provided details.
- Updating the terraform file and running
terraform apply
Note: Terraform's json syntax would be used.
Our code would be written in Python, because it's much easy to manipulate json in and it's fast to write.