-
-
Save yannhowe/5ab1501156bd84c8ac261e2c17b8e3e0 to your computer and use it in GitHub Desktop.
| # Image neeeds to have ssh-client | |
| image: docker:git | |
| services: | |
| - docker:dind | |
| stages: | |
| - staging | |
| before_script: | |
| - docker login -u gitlab-ci-token -p $CI_BUILD_TOKEN $CI_REGISTRY | |
| - mkdir -p ~/.ssh | |
| # Paste the PRIVATE key into a gitlab variable. Pay attention to the linebreak at the end when pasting | |
| - echo "$DEPLOY_SERVER_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa | |
| - chmod 600 ~/.ssh/id_rsa | |
| - eval "$(ssh-agent -s)" | |
| - ssh-add ~/.ssh/id_rsa | |
| - ssh-keyscan -H 'your.server.hostname' >> ~/.ssh/known_hosts | |
| staging: | |
| stage: staging | |
| tags: | |
| - docker | |
| only: | |
| - staging | |
| script: | |
| - docker build --pull -t $CI_REGISTRY_IMAGE:staging . | |
| - docker push $CI_REGISTRY_IMAGE:staging | |
| # your own server details here | |
| - ssh $SERVER_USER@$SERVER_HOSTNAME < deploy.sh |
echo ${ID_RSA_DEVELOP} > id_rsa
now id_rsa file is one line,
run this command to check , openssl rsa -in id_rsa -text -noout
output unable to load Private Key
我解决这个问题:
- echo ${ID_RSA_DEVELOP} > id_rsa
此时, id.pub 文件格式为1行, job运行时, 报出 密钥文件 出错
此时, 我更改如下: - echo "${ID_RSA_DEVELOP}" > id_rsa
问题得到解决
cat ~/.ssh/id.pub , 格式正确
@amatiash i followed your method but i got the following response
Running hooks in /etc/ca-certificates/update.d... done. $ mkdir -p ~/.ssh $ echo "$SSH_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa $ chmod 700 ~/.ssh/id_rsa $ eval $(ssh-agent -s) Agent pid 3067 $ ssh-add ~/.ssh/id_rsa Enter passphrase for /root/.ssh/id_rsa: ERROR: Job failed: exit code 1Why does it request for passphrase?
yo, it looks like the ssh key you created to use was created with a password, you might want to create a new ssh key that doesn't use a password. It is recommended that you don't use a password for SSH keys for server communication because it will error out the process since you can't put the password in manually when it ask for it when Gitlab's runner process is going. I had this issue a few weeks ago; so this is why I am suggesting that to you.
this worked for me:
`
deploy:
image: docker:stable
- services: docker/dind
stage: deploy
script:
- echo "$RELEASE_IMAGE"
- 'which ssh-agent || ( apk --update add openssh-client )'
- eval $(ssh-agent -s)
- mkdir -p ~/.ssh
- echo "$SERVER_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa
- chmod 700 ~/.ssh/id_rsa
- eval "$(ssh-agent -s)"
- ssh-add ~/.ssh/id_rsa
- ssh-keyscan -H 'YOUR_IP_ADDRESS' >> ~/.ssh/known_hosts
- ssh-keyscan YOUR_IP_ADDRESS | sort -u - ~/.ssh/known_hosts -o ~/.ssh/known_hosts
- '[[ -f /.dockerinit ]] && echo -e "Host *\n\tStrictHostKeyChecking no\n\n" > ~/.ssh/config'
`
If you need to enter the password, then you have to. I found a way how to do that.
before_script:
- 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client -y )'
- 'which sshpass || ( apt-get update -y && apt-get install sshpass -y )'
- mkdir -p ~/.ssh
- echo "$SSH_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa
- chmod 700 ~/.ssh/id_rsa
- eval $(ssh-agent -s)
- ssh-add ~/.ssh/id_rsa
- ssh-keyscan -H 'gitlab.com' >> ~/.ssh/known_hosts
- ssh-keyscan gitlab.com | sort -u - ~/.ssh/known_hosts -o ~/.ssh/known_hosts
- rm -rf .git
- '[[ -f /.dockerenv ]] && echo -e "Host *\n\tStrictHostKeyChecking no\n\n" > ~/.ssh/config'
script:
- sshpass -p "<your password goes here>" ssh username@hostname "your commands"I used sshpass
I generated ssh keys that didn't need a password so I used that code above without sshpass, but am receiving this issue:
Warning: Permanently added the ECDSA host key for IP address '##.##.###.##' to the list of known hosts.
Permission denied, please try again.
Permission denied, please try again.
Permission denied (publickey,password).
Code:
before_script:
- 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client -y )'
- mkdir -p ~/.ssh
- echo "$SSH_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa
- chmod 700 ~/.ssh/id_rsa
- eval $(ssh-agent -s)
- ssh-add ~/.ssh/id_rsa
- ssh-keyscan -H 'host.host.com' >> ~/.ssh/known_hosts
- ssh-keyscan host.host.com | sort -u - ~/.ssh/known_hosts -o ~/.ssh/known_hosts
- rm -rf .git
- '[[ -f /.dockerenv ]] && echo -e "Host *\n\tStrictHostKeyChecking no\n\n" > ~/.ssh/config'
testSSH:
script:
- ssh [email protected] "cd Desktop/testssh && git pull origin master"
I have been troubleshooting for hours and cannot resolve the issue. Could anyone please help?
If you need to enter the password, then you have to. I found a way how to do that.
before_script: - 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client -y )' - 'which sshpass || ( apt-get update -y && apt-get install sshpass -y )' - mkdir -p ~/.ssh - echo "$SSH_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa - chmod 700 ~/.ssh/id_rsa - eval $(ssh-agent -s) - ssh-add ~/.ssh/id_rsa - ssh-keyscan -H 'gitlab.com' >> ~/.ssh/known_hosts - ssh-keyscan gitlab.com | sort -u - ~/.ssh/known_hosts -o ~/.ssh/known_hosts - rm -rf .git - '[[ -f /.dockerenv ]] && echo -e "Host *\n\tStrictHostKeyChecking no\n\n" > ~/.ssh/config' script: - sshpass -p "<your password goes here>" ssh username@hostname "your commands"I used sshpass
how can i use a different ssh port (like 2222) ??
useful tip, thanks
If you need to enter the password, then you have to. I found a way how to do that.
before_script: - 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client -y )' - 'which sshpass || ( apt-get update -y && apt-get install sshpass -y )' - mkdir -p ~/.ssh - echo "$SSH_PRIVATE_KEY" | tr -d '\r' > ~/.ssh/id_rsa - chmod 700 ~/.ssh/id_rsa - eval $(ssh-agent -s) - ssh-add ~/.ssh/id_rsa - ssh-keyscan -H 'gitlab.com' >> ~/.ssh/known_hosts - ssh-keyscan gitlab.com | sort -u - ~/.ssh/known_hosts -o ~/.ssh/known_hosts - rm -rf .git - '[[ -f /.dockerenv ]] && echo -e "Host *\n\tStrictHostKeyChecking no\n\n" > ~/.ssh/config' script: - sshpass -p "<your password goes here>" ssh username@hostname "your commands"I used sshpass
how can i use a different ssh port (like 2222) ??
Use
script:
- sshpass -p "<your password goes here>" ssh -p2222 username@hostname "your commands"
I had to also run this on the deployment server
https://stackoverflow.com/questions/44363537/gitlab-ci-ssh-permission-denied-publickey-password
cat ~/.ssh/id_rsa.pub > ~/.ssh/authorized_keys
This did the trick!
$ echo "$TEST_SSH_PRIVATE_KEY" | tr -d '\r' | ssh-add - >/dev/null
Error loading key "(stdin)": invalid formatI have had the same error.
You added TEST_SSH_PRIVATE_KEY as protected variable to the GitLab CI/CD config. This is fine. But the variable then only gets exposed to protected branches (masterfor example is per default) and protected tags. I configured thev*wildcard (matches my use case) as protected tags and it did run.
This worked
$ echo "$TEST_SSH_PRIVATE_KEY" | tr -d '\r' | ssh-add - >/dev/null
Error loading key "(stdin)": invalid formatI have had the same error.
You added TEST_SSH_PRIVATE_KEY as protected variable to the GitLab CI/CD config. This is fine. But the variable then only gets exposed to protected branches (masterfor example is per default) and protected tags. I configured thev*wildcard (matches my use case) as protected tags and it did run.
It worked for me
So sorry I can't really contribute guys cos I've moved on to other tools and things over the past few years after a short time kicking the tires on gitlab. This gist has really taken on a mind of its own. Glad it facilitated some useful discussion.
Which tool do use you now for CI/CD? I'm tired with Jenkins, yet moved to Gitlab CI/CD but the SSH way was just too f**king dumb.
Hey all, just tackled this today. FYI, this is how you can do git operations (i.e. tagging) from within CI as of today (variable of type 'File'):
tagging_job:
stage: release
image: ubuntu
before_script:
- mkdir -p ~/.ssh
# Settings > Repository > Deploy Keys > "DEPLOY_KEY_PUBLIC" is the public key of the utitlized SSH pair (choose `Write access allowed` on creation)
# Settings > CI/CD > Variables > "DEPLOY_KEY_PRIVATE" is the private key of the utitlized SSH pair, type is 'File' and ends with empty line
- mv "$DEPLOY_KEY_PRIVATE" ~/.ssh/id_rsa
- chmod 600 ~/.ssh/id_rsa
- 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client git -y )'
- eval "$(ssh-agent -s)"
- ssh-add ~/.ssh/id_rsa
- ssh-keyscan -H 'gitlab.com' >> ~/.ssh/known_hosts
script:
# try to connect to GitLab.com
- ssh [email protected]
# fresh clone
- mkdir ~/source && cd $_
- git clone [email protected]:$CI_PROJECT_PATH.git
- cd $CI_PROJECT_NAME
# Version tag
- git tag my-tag
- git push --tags -o ci.skipThe -o ci.skip part causes the generated pipeline to be skipped (not auto-ran). If you want to not generate a pipeline at all for your tag push, add this to the top of the .gitlab-ci.yml:
workflow:
rules:
- if: $CI_COMMIT_TAG
when: never
- when: alwaysPeace
I had to also run this on the deployment server
https://stackoverflow.com/questions/44363537/gitlab-ci-ssh-permission-denied-publickey-passwordcat ~/.ssh/id_rsa.pub > ~/.ssh/authorized_keysThis did the trick!
Hi Guys
This trick works...try it.
thanks @sofyansitorus
$ echo "$TEST_SSH_PRIVATE_KEY" | tr -d '\r' | ssh-add - >/dev/null
Error loading key "(stdin)": invalid formatI have had the same error.
You added TEST_SSH_PRIVATE_KEY as protected variable to the GitLab CI/CD config. This is fine. But the variable then only gets exposed to protected branches (masterfor example is per default) and protected tags. I configured thev*wildcard (matches my use case) as protected tags and it did run.
This was exactly what is going on for me. And anyone else that feels like they need to unprotect their variable, don't do that. Just go configure your protected branches and tags to inject these variables like @richardhj said.
eval $(ssh-agent -s) echo "$SSH_PRIVATE_KEY" | tr -d '\r' | ssh-add - > /dev/null mkdir -p ~/.ssh chmod 700 ~/.ssh ssh-keyscan xxx.xxx.xxx.xxx >> ~/.ssh/known_hosts chmod 644 ~/.ssh/known_hosts
is worked for me
( add a SSH_PRIVATE_KEY in var settings )
Thanks @amatiash !
How to add multiple Private keys to known_host??
Hey all, just tackled this today. FYI, this is how you can do git operations (i.e. tagging) from within CI as of today (variable of type 'File'):
tagging_job: stage: release image: ubuntu before_script: - mkdir -p ~/.ssh # Settings > Repository > Deploy Keys > "DEPLOY_KEY_PUBLIC" is the public key of the utitlized SSH pair (choose `Write access allowed` on creation) # Settings > CI/CD > Variables > "DEPLOY_KEY_PRIVATE" is the private key of the utitlized SSH pair, type is 'File' and ends with empty line - mv "$DEPLOY_KEY_PRIVATE" ~/.ssh/id_rsa - chmod 600 ~/.ssh/id_rsa - 'which ssh-agent || ( apt-get update -y && apt-get install openssh-client git -y )' - eval "$(ssh-agent -s)" - ssh-add ~/.ssh/id_rsa - ssh-keyscan -H 'gitlab.com' >> ~/.ssh/known_hosts script: # try to connect to GitLab.com - ssh [email protected] # fresh clone - mkdir ~/source && cd $_ - git clone [email protected]:$CI_PROJECT_PATH.git - cd $CI_PROJECT_NAME # Version tag - git tag my-tag - git push --tags -o ci.skipThe
-o ci.skippart causes the generated pipeline to be skipped (not auto-ran). If you want to not generate a pipeline at all for your tag push, add this to the top of the.gitlab-ci.yml:workflow: rules: - if: $CI_COMMIT_TAG when: never - when: alwaysPeace
Thx, you made my day !
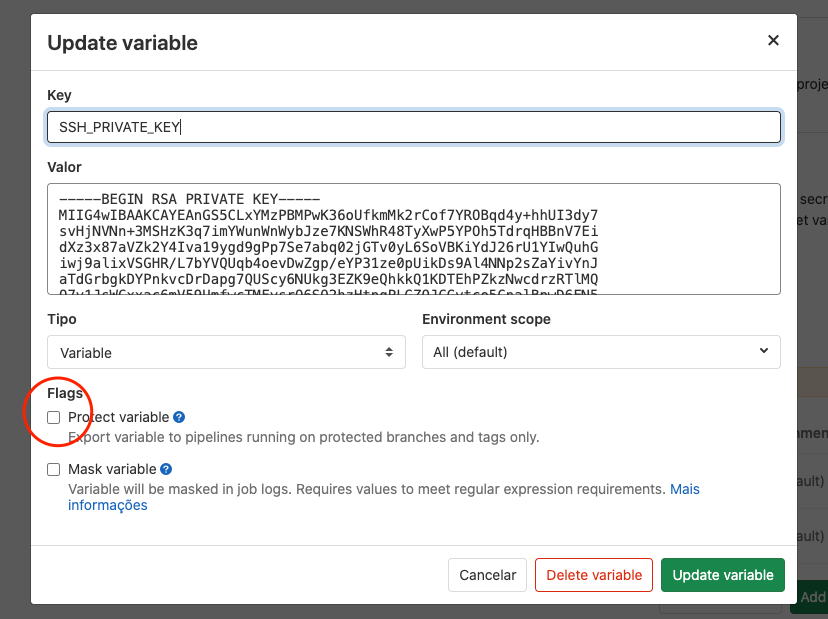
So now it fixes or not?