- editor setup
- compilation database
- vscode debugger
- debug cctest
- debug mjsunit
- testing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| import re, subprocess, idaapi, ida_segment, ida_kernwin | |
| # To install this, simply put it in your ida_install/loaders folder and open | |
| # a `/proc/<pid>/mem` file! | |
| # | |
| # You might need to set `echo 0 > /proc/sys/kernel/yama/ptrace_scope` if you | |
| # want to be able to dump processes depending on your system configuration. | |
| # Check if the file is supported by our loader | |
| def accept_file(li, filename): |
- yoyoyoyo
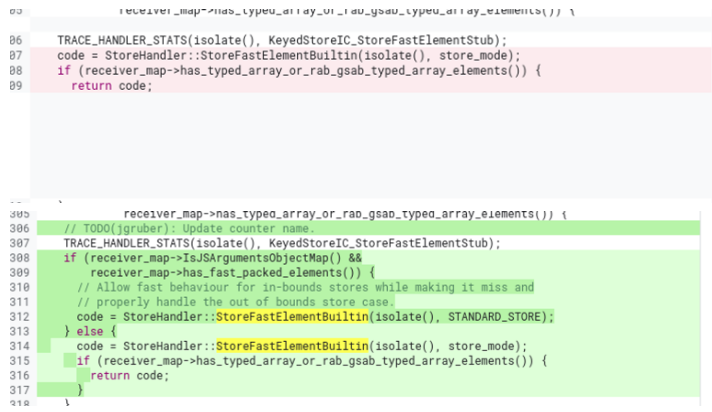
Official patch: https://chromium-review.googlesource.com/c/v8/v8/+/4584248
Patch come from KeyedStoreIC::StoreElementHandler(), it returns fast path code(Turbofan builtin) for keyed store depends on "receiver_map" and "store_mode". Based on the content of this function is all about element STORE, I personally believe that this is an OOB writes vulnerability.
If we divide the PoC exploration into two parts based on this func, they are:
test.js
var arr = new Array(1.1, 2.2, 3.3);
function test(obj) {
arr[0] = obj;
}
test({});Print bytecode of test function:
IERAE CTF had one of the coolest pwn challenges I've done in the while. It was written by hugeh0ge.
Here's the full source:
// gcc chal.c -fno-stack-protector -static -o chal
#include <stdio.h>
#include OlderNewer