- Go to Network - WAN - WAN Connection
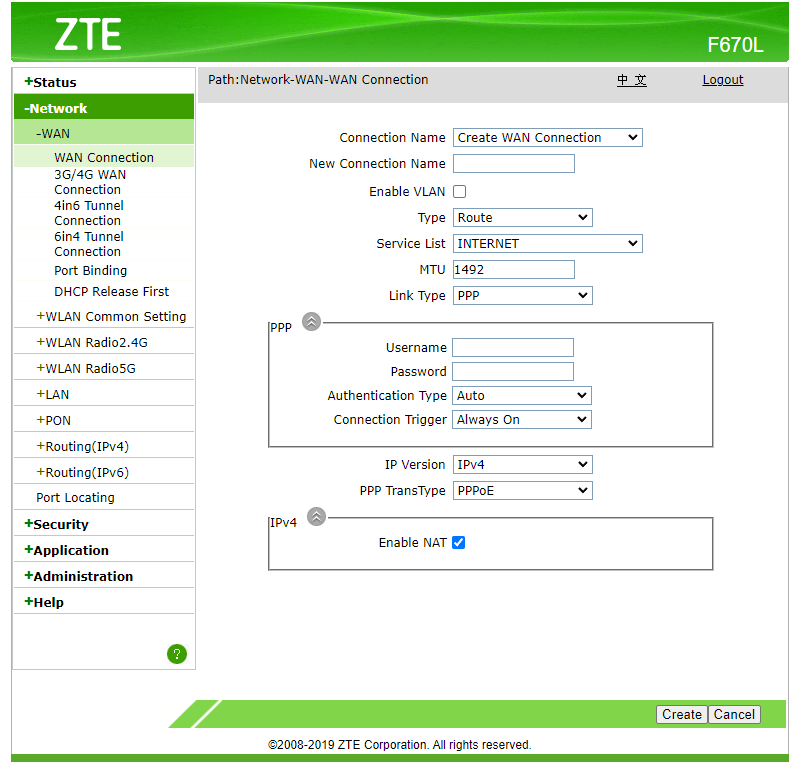
- Right click Type Route dropdown select and click "Inspect" in the context menu.
In console, run the code below:document.getElementById('Frm_mode').options[document.getElementById('Frm_mode').options.selectedIndex].setAttribute('value', 'BRIDGE'); Change_mode();
- Input New Connection Name. Example:
Bridge. Click Create.
| apiVersion: apps/v1 | |
| kind: DaemonSet | |
| metadata: | |
| labels: | |
| component: resolv | |
| tier: node | |
| name: resolv | |
| namespace: default | |
| spec: | |
| selector: |
- I faced bandwidth issues between a WG Peer and a WG server. Download bandwidth when downloading from WG Server to WG peer was reduced significantly and upload bandwidth was practically non existent.
- I found a few reddit posts that said that we need to choose the right MTU. So I wrote a script to find an optimal MTU.
- Ideally I would have liked to have run all possible MTU configurations for both WG Server and WG Peer but for simplicity I choose to fix the WG Server to the original 1420 MTU and tried all MTUs from 1280 to 1500 for the WG Peer.
- On WG server, I started an
iperf3server - On WG peer, I wrote a script that does the following:
wg-quick down wg0
- Edit MTU in the
/etc/wireguard/wg0.conffile
Instructions to obtain WireGuard details of your NordVPN account. These can be used to setup a WireGuard tunnel on your router to NordVPN.
Source: https://forum.gl-inet.com/t/configure-wireguard-client-to-connect-to-nordvpn-servers/10422/27
If you have any linux machine, use that or install a vm if you don't have one.
Get their official linux app installed. Make sure you have wireguard installed too. And set the used technology to Nordlynx by running nordvpn set technology nordlynx
| CC = gcc | |
| RM = rm -f | |
| INSTRUMENT_FOR_PROMETHEUS := false | |
| ifeq ($(INSTRUMENT_FOR_PROMETHEUS),true) | |
| CFLAGS = -Wall -DINSTRUMENT_FOR_PROMETHEUS | |
| LIBS = -lbcm2835 -lprom -lpromhttp -lmicrohttpd | |
| else | |
| CFLAGS = -Wall |
Total number of IPv4 addresses: 100,750,168. That’s the equivalent of just over six /8’s Also see this blog: https://toonk.io/aws-and-their-billions-in-ipv4-addresses/
just for fun, let's put a value number on that
Total value at, $20 per IP: => $2,015,003,360
Total value at, $25 per IP: => $2,518,754,200
| package main | |
| import ( | |
| "net/http" | |
| "github.com/prometheus/client_golang/prometheus" | |
| "github.com/prometheus/client_golang/prometheus/promhttp" | |
| "log" | |
| "time" | |
| "math/rand" |
| { | |
| "puppet_task_version": 1, | |
| "supports_noop": false, | |
| "description": "Stop or restart a service or list of services on a node.", | |
| "parameters": { | |
| "service": { | |
| "description": "The name of the service, or a list of service names to stop.", | |
| "type": "Variant[Array[String],String]" | |
| }, | |
| "norestart": { |
| % docker build -t rust . | |
| ... | |
| # Export the image to tarball, which itself contains tarballs and a manifest.json | |
| % docker save -o rust.tar rust | |
| # Extract the last layer | |
| # tar's -O flag extracts a single entry from the tarball. | |
| # The file we want is the last "Layer" in the manifest.json | |
| % tar -xf rust.tar -O $(tar -xf rust.tar -O manifest.json | jq -r '.[].Layers[-1]') > curlbash.tar |