You may want to use AdGuard's DNS over HTTPS1 service if you
- Want to make it harder for your ISP to know what websites you are requesting
- Want to block most traditional ads from your web browsing experience across your entire PC
- Open PowerShell

- Add the primary and secondary AdGuard DNS IPv4 and IPv6 addresses2
netsh dns add encryption server=94.140.14.14 dohtemplate=https://dns.adguard.com/dns-query autoupgrade=yes udpfallback=no netsh dns add encryption server=94.140.15.15 dohtemplate=https://dns.adguard.com/dns-query autoupgrade=yes udpfallback=no netsh dns add encryption server=2a10:50c0::ad1:ff dohtemplate=https://dns.adguard.com/dns-query autoupgrade=yes udpfallback=no netsh dns add encryption server=2a10:50c0::ad2:ff dohtemplate=https://dns.adguard.com/dns-query autoupgrade=yes udpfallback=no - Verify addition of DNS options
netsh dns show encryptionEncryption settings for 94.140.15.15 ---------------------------------------------------------------------- DNS-over-HTTPS template : https://dns.adguard.com/dns-query Auto-upgrade : yes UDP-fallback : no Encryption settings for 94.140.14.14 ---------------------------------------------------------------------- DNS-over-HTTPS template : https://dns.adguard.com/dns-query Auto-upgrade : yes UDP-fallback : no Encryption settings for 2a10:50c0::ad1:ff ---------------------------------------------------------------------- DNS-over-HTTPS template : https://dns.adguard.com/dns-query Auto-upgrade : yes UDP-fallback : no Encryption settings for 2a10:50c0::ad2:ff ---------------------------------------------------------------------- DNS-over-HTTPS template : https://dns.adguard.com/dns-query Auto-upgrade : yes UDP-fallback : no- If you don't see the new DNS options, you may need to run PowerShell with administrator priviledges
- Open Settings > Network & internet > Wi-Fi > Hardware properties

- Click the "Edit" button in the DNS servers block
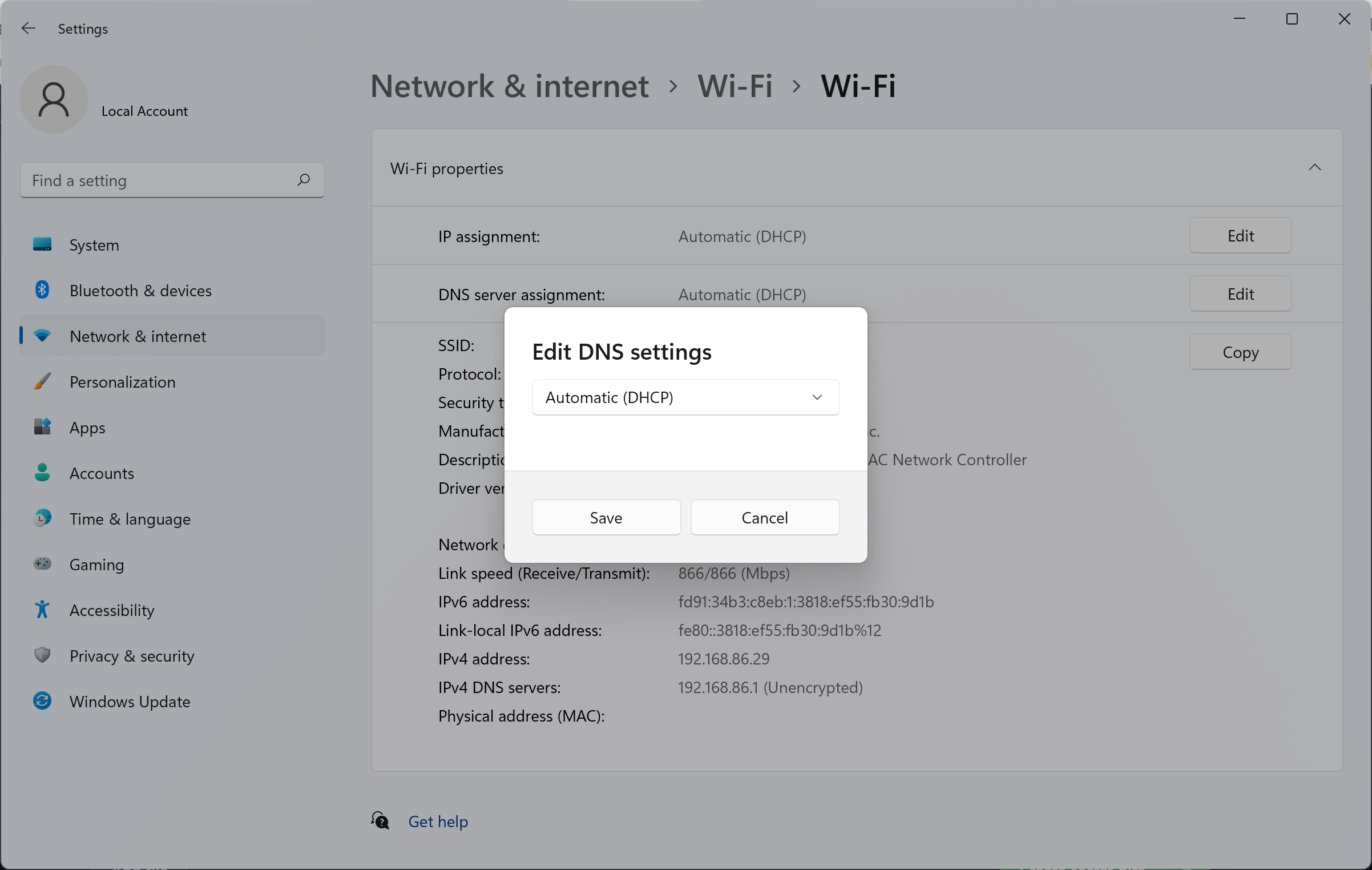
- Change the dropdown setting from "Automatic (DHCP)" to "Manual"

- Ensure both IPv4 and IPv6 are toggled on

- Under IPv4, enter
94.140.14.14for the Preferred DNS, and94.140.15.15for the Alternate DNS
- Under IPv6, enter
2a10:50c0::ad1:fffor the Preferred DNS, and2a10:50c0::ad2:fffor the Alternate DNS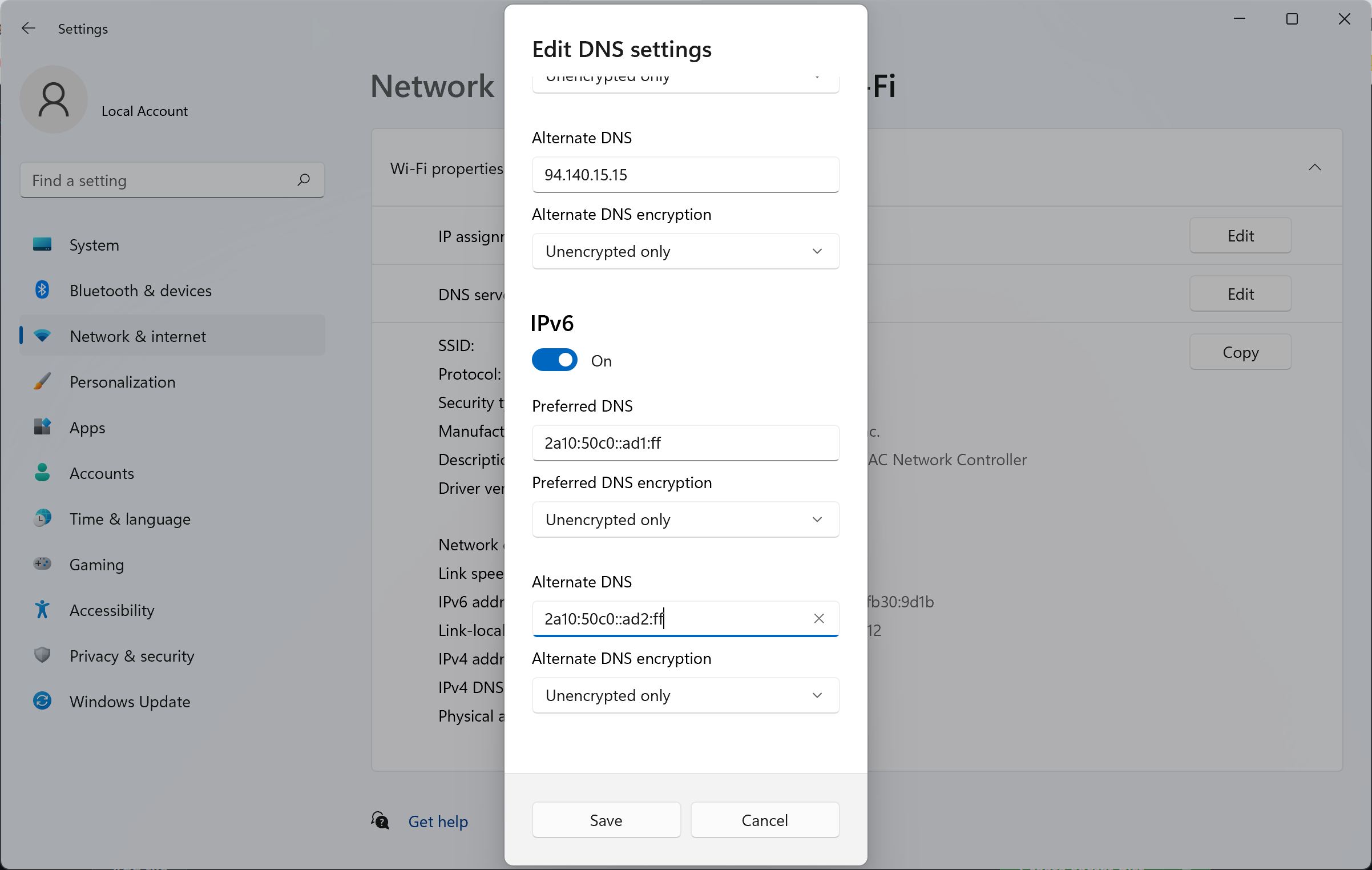
- Ensure all of the DNS encryption dropdowns are set to "Encrypted only (DNS over HTTPS)"

- Click "Save"




thanks